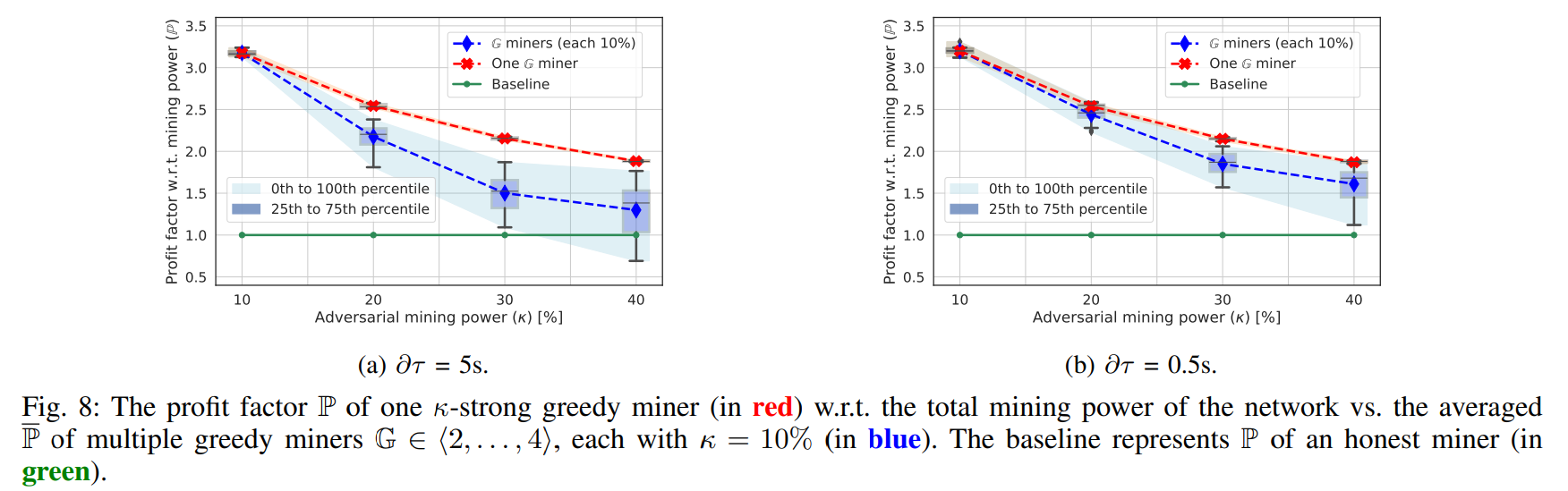
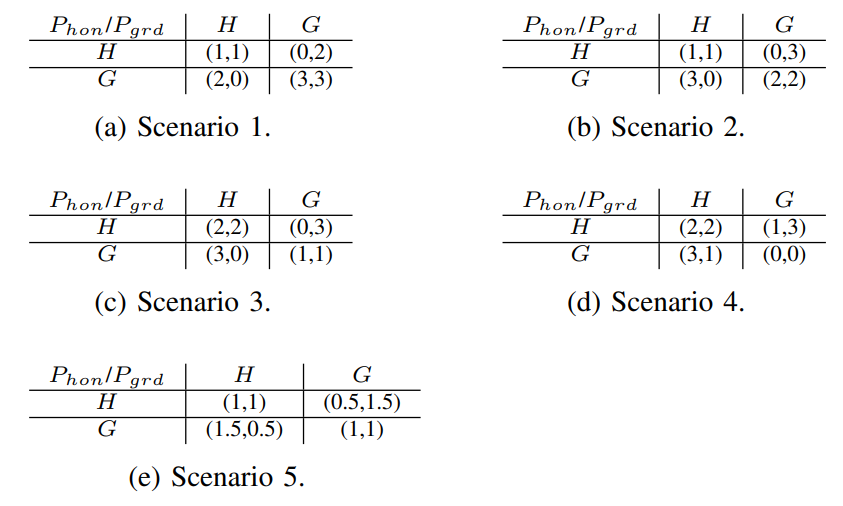
Simulation Model for DAG-PROTOCOL Under Incentive Attacks
Table of Links
Abstract and I. Introduction
II. Background
III. Problem Definition
IV. DAG-Oriented Solutions
V. Game...
Your resource for web content, online publishing
and the distribution of digital products.
and the distribution of digital products.
Newswire > September, 2024
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.