and the distribution of digital products.
DM Television
Your Docker Containers Are Probably Full of Security Holes—Here’s How to Fix Them Now
- ==Docker Scouts primarily helps scan images for vulnerabilities==. These vulnerabilities could pose a risk to security before the software begins its development. Besides, it scans for CVEs and makes sure that known security issues are dealt with before reaching the production stage.
- Moreover, ==Docker Scout sustains compliance by generating a complete Software Bill of Materials (SBOM)==. These specify the container images' dependencies and assist you in evaluating risks related to third-party libraries as well as containment within security standards. In addition, these preserve security policies by making certain that container images adhere to set compliance and security policies. These policies are customizable and typically depend on the preferred security settings for your organization.
- ==Automated security scans are easily adjustable with Docker Scout==. Since it enables integrations with CI/CD pipelines which scan for security flaws within the software development lifecycle while building and deploying. With the needs of the project scoped, issues can be resolved early on and security is ensured.
- ==With the assistance of Docker Scout, unwanted exposure to vulnerabilities is kept under control==. So, thanks to the provided guidance on how to deactivate, patch, or update components to minimize danger and improve security.
As the DevOps world continues to evolve, container security has taken center stage. These containers are used commonly and usually come with new security risks. As cyber threats are on the rise, weaknesses in containerized settings can put applications at risk. Docker Scout helps mitigate these gaps.
\ These act as an advanced tool designed to improve container security. Docker Scout supports vulnerability detection, Software Bill of Materials generation, and policy enforcement which makes the process of securing Docker containers more streamlined and effective.
\ This guide will demonstrate how to make use of particular features of Docker Scout. Setup, configuration, and other tips and tricks will also be discussed. You will learn how to integrate Docker Scout into your DevOps workflows. Let’s jump right in.
Understanding Docker Scout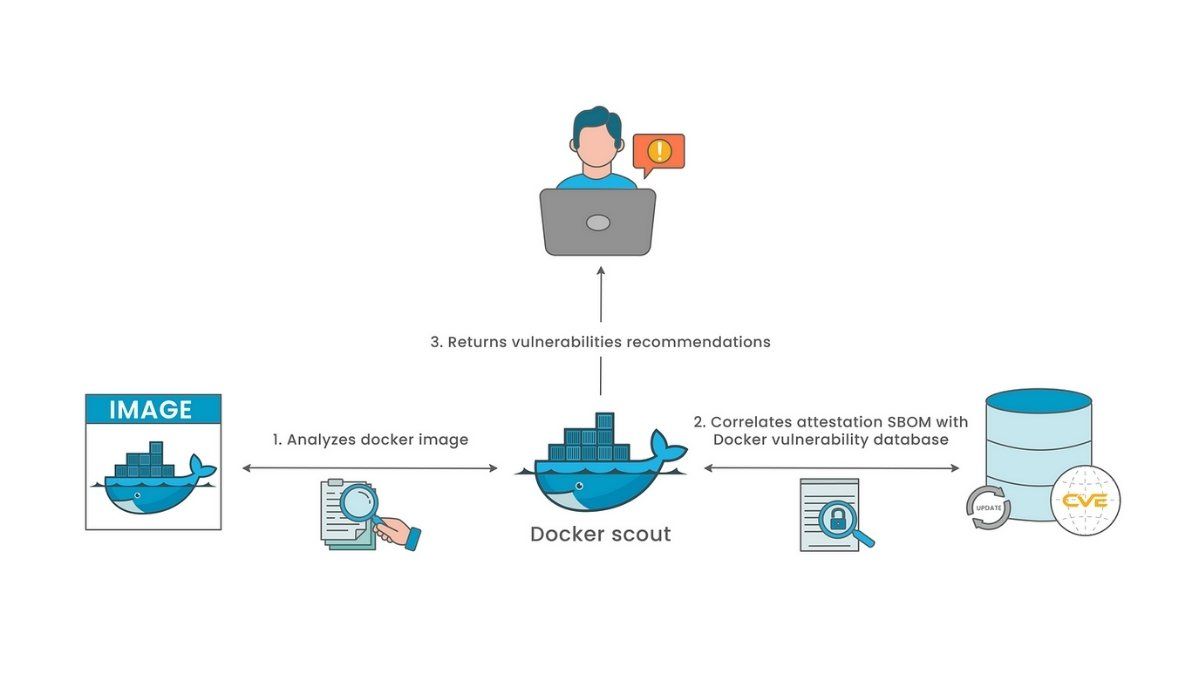
\ Docker Scout enables you to maximize security for your containers by aiding in vulnerability, dependency, and compliance analysis. Its seamless integration with Docker makes Scout a must-have toolbox for your security requirements.
What Is Docker Scout?Docker Scout is a security tool for Docker containers. It scans container images to identify vulnerabilities. Moreover, it creates an SBOM and follows security policies. With Docker Scout, managing and monitoring containerized application risks become manageable and straightforward.
\ These Scouts enable users to avoid vulnerabilities by tracking their Docker images. Furthermore, it provides an effortless integration into your workflow with real-time scanning of vulnerabilities and providing further details about the components of the software in that container.
\ It also lets users keep track of and evaluate all components and dependencies embedded in the application. They can make sure no vulnerable fragments are included by generating a Software Bill of Materials (SBOM).
\ Moreover, Docker Scout’s policy enforcement features verify that images of containers are “locked-in”. So, it helps teams comply with industry best practices and protect them from security threats. With Docker Scout, securing containerized applications can be made easily and proactively.
Key Features of Docker Scout- ==Vulnerability Scanning==: Docker Scout detects known vulnerabilities in your containers.
- ==SBOM Generation==: Docker Scout generates a detailed Software Bill of Materials.
- ==Policy Enforcement==: Docker Scout ensures your images meet defined security standards.
\ Docker Scout works well within the Docker ecosystem. It integrates meticulously into your existing tools and workflows. Therefore, it simplifies security without slowing down development.
How To Set Up Docker Scout?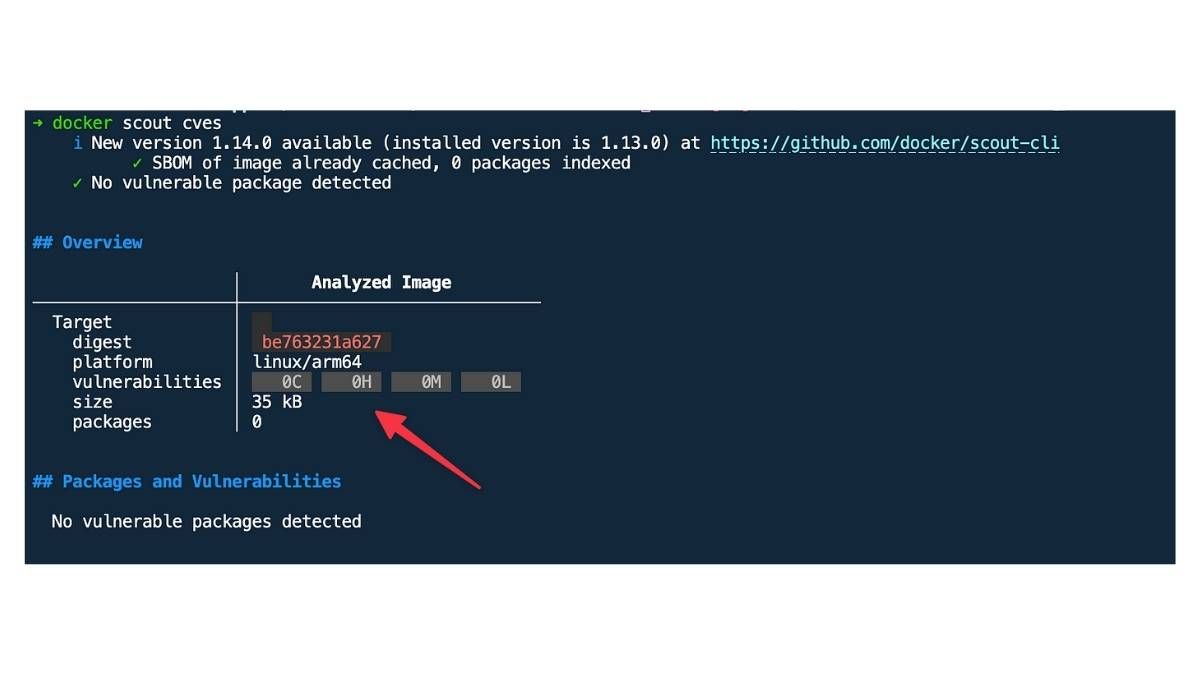
Setting up Docker Scout is quick and simple. Here are the most common steps to get started.
Installation and PrerequisitesBefore installing Docker Scout, make sure your Docker is running as intended. Docker Scout works with Docker Desktop or Docker Engine.
To install Docker Scout, run this command:
docker scout initThis installs Docker Scout and all its dependencies. You’re now ready to begin scanning images.
Running Your First ScanTo run your first scan, use the command.
docker scout quickviewThis will give you a quick security overview of your image.
\ For example, to scan my-app:latest, run:
docker scout quickview my-app:latest\ This command will scan your Docker image and provide a summary of vulnerabilities and compliance issues.
Understanding the Scan ResultsThe results of the scan are presented in sections:
- ==Vulnerabilities==: Shows any CVEs found in your image.
- ==SBOM==: Displays the Software Bill of Materials for the image.
- ==Policy Violations==: Lists any security policy violations.
\ These results help you understand the security state of your Docker images. Docker Scout has several key features that help secure container images. Let’s explore them.
Vulnerability Scanning
\ Docker Scout scans images for known vulnerabilities. It looks at each package it scans and checks it against the CVE database. When it finds a match, it flags the harm and shows the severity level alongside ways to fix it. This helps mitigate issues before they hit production.
Software Bill of Materials (SBOM)Docker Scout produces a unique SBOM for each scanned image. This information outlines all the software components that form the image.
The SBOM is useful for tracking all dependencies to facilitate the identification of vulnerabilities in third-party packages. This in turn is very fundamental for improving supply chain security and image integrity.
Security Policies and Remediation SuggestionsWith Docker Scout, security policies can be set and potential risks, such as acceptable vulnerability ratings, can be determined. If an image violates a policy, remediation steps are suggested by Docker Scout. This allows for best security practices to be established for containers before they are deployed.
Integrating Docker Scout into CI/CD PipelinesAutomating security checks in your CI/CD pipeline is crucial. Docker Scout fits naturally into DevOps workflows. By integrating Docker Scout, you ensure that security is part of your pipeline from the beginning.
Using Docker Scout with GitHub Actions/GitLab CI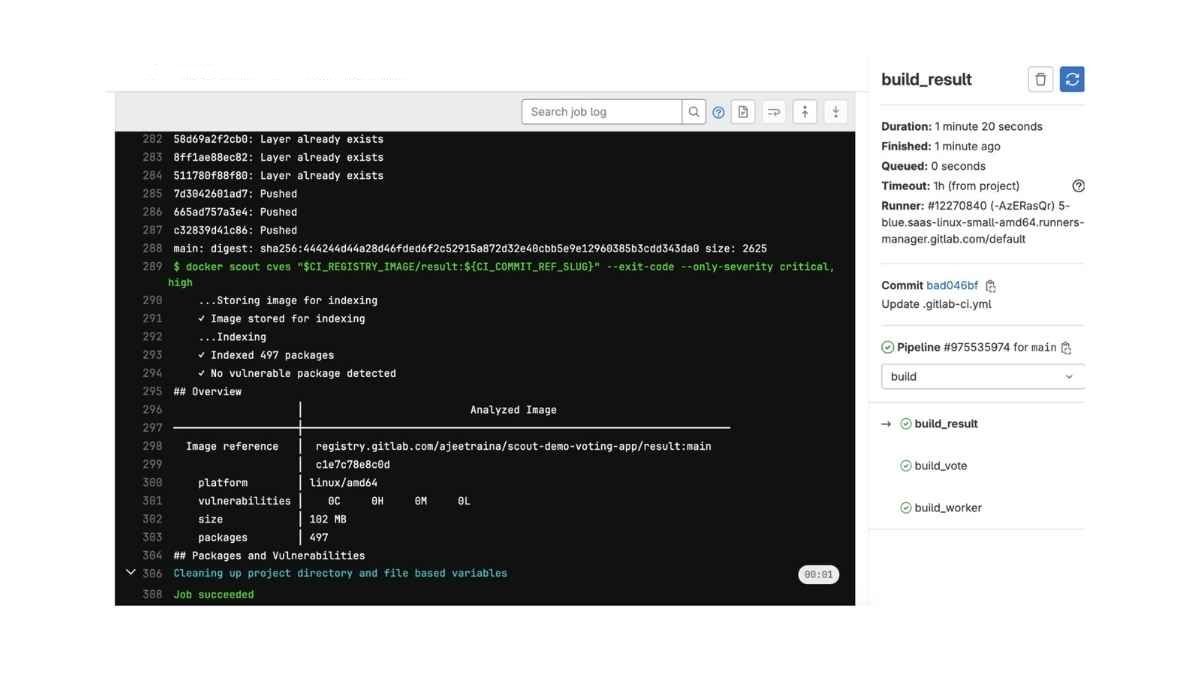
Integrating Docker Scout with GitHub Actions or GitLab CI automates security in the build process. For example, in GitHub Actions you can perform a Docker Scout scan on every push. This makes certain that your images are secure before deployment.
\ Here’s a basic GitHub Actions configuration:
name: Docker Security Scan on: push: branches: - main jobs: security-scan: runs-on: ubuntu-latest steps: - name: Checkout code uses: actions/checkout@v2 - name: Run Docker Scout Scan run: | docker scout init docker scout quickview my-app:latestThis configuration runs a security scan each time changes are pushed to the main branch.
Automating Security Checks Before DeploymentIntroducing Docker Scout into your CI/CD pipeline helps catch security issues early. Each time a new image is built or updated, Docker Scout scans it. If vulnerabilities are found, the build fails. This prevents insecure images from being deployed to production.
\ Here’s an example configuration for GitLab CI:
stages: - scan docker_scan: stage: scan script: - docker scout init - docker scout quickview my-app:latestWith this setup, Docker Scout runs automatically as part of the build process.
Best Practices for Secure Container Image DevelopmentWhile Docker Scout helps identify vulnerabilities, there are other practices to follow to reduce security risks.
Reducing Attack SurfacesMinimize the number of dependencies in your images. The fewer libraries you include, the fewer potential vulnerabilities there are. Use minimal base images like Alpine, and only include essential components.
Regular Updates and PatchingContainer security is an ongoing effort. Regularly update your images to include the latest patches. Docker Scout helps track vulnerabilities, so you can stay on top of necessary updates.
Leveraging Docker Scout’s InsightsUse Docker Scout’s results to continuously improve your security posture. Review vulnerability reports, address remediation suggestions, and update your policies regularly. Continuous scanning and improvement validate that your images stay secure.
ConclusionDocker Scout offers container security tools that assist DevOps teams improve the overall protection of Docker for their images. It automatically scans for vulnerabilities and enforces policies, making the task remarkably easier. Implementing Docker Scout into your existing CI/CD pipelines confirms that security is built within your development processes.
\ Moreover, Docker Scout acts as a tool for container security. These allow users to actively mitigate possible breaches. Images are checked for and scanned for vulnerabilities, in addition to ensuring policies are being followed throughout the lifecycle of the development. Docker Scout gives users the ability to build, test, and deploy secure applications in a matter of hours. Therefore, these improve productivity.
FAQ’sHow does Docker Scout detect vulnerabilities in Docker images?
Docker Scout scans the container image for known CVEs. It is done by comparing the image’s components against the CVE database.
\
Can I integrate Docker Scout into a CI/CD pipeline?
Yes, Docker Scout can be seamlessly integrated with CI/CD pipelines. For example, these are incorporated with GitHub Actions and GitLab CI to run automated security scans during the build process.
\
What is a Software Bill of Materials (SBOM) in Docker Scout?
An SBOM keeps track of all the software constituents and dependencies present in a docker image. So, it assists you in monitoring the weaknesses linked to external libraries.
\
How do I configure Docker Scout to enforce security policies?
You can define custom security policies in Docker Scout. These help enforce rules such as allowed vulnerability severity levels, and minimum patch versions for dependencies.
\
What happens if Docker Scout finds vulnerabilities in an image?
Docker Scout highlights existing vulnerabilities. They also provide a severity rating. So, these offer remediation steps to aid you in resolving the problems before container deployment.
\
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.