and the distribution of digital products.
DM Television
Understanding Nillion: A Comprehensive Overview
- Nillion has partnered with Virtuals, NEAR, Aptos, Arbitrum, Ritual, io.net, and Meta, among others.
- A suite of application tools, including nilAI, nilVM, nilDB, and nilChain, provides developers with the resources to create privacy-preserving applications across sectors such as AI, healthcare, and DeFi.
- The network utilizes an orchestration of Privacy-Enhancing Technologies (PETs), including Multi-Party Computation (MPC), Homomorphic Encryption, and Zero-Knowledge Proofs to facilitate secure data computation and storage across its decentralized infrastructure.
- Nillion’s Verifier Program reached ~500,000 Verifiers actively contributing to the network, collectively processing ~195 million Secrets and securing ~1,050 GB of data.
Handling high value data (e.g., passwords, personalized AI, healthcare information, and biometrics) has traditionally been both insecure and inefficient. While encryption secures stored data, it requires decryption for computation and re-encryption afterward, introducing vulnerabilities and delays. Although blockchain technology decentralizes transaction and data management, it does not inherently solve the challenges of secure computation on encrypted data. This constraint limits the type of applications that can be safely built within Web3.
Nillion addresses these limitations by enabling data transfer, storage, and computation without decryption, guaranteeing that sensitive information remains private and secure throughout its entire lifecycle. This approach, known as Blind Compute, decentralizes trust and expands the use cases for decentralized networks to previously untapped 'whitespace' areas like private AI agents, private LLM inference, and other industries that require secure data. By using advanced Privacy-Enhancing Technologies (PETs) such as Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Trusted Execution Environments (TEEs), Nillion allows data to remain encrypted even during computation.
Website / X (Twitter) / Discord
BackgroundNillion, founded in 2021, is a network that provides a novel way to handle private data across distributed systems without compromising security or efficiency. Supported by application frameworks such as nilVM, nilDB, nilAI, and nilChain, Nillion equips developers with tools to build privacy-preserving applications across sectors like AI, DeFi, and data storage.
The project’s team comprises Alex Page (CEO), former Hedera SPV General Partner and Goldman Sachs Banker; Andrew Masanto (CSO), Co-Founder of Hedera and Founding CMO of Reserve; Slava Rubin (CBO), Founder of Indiegogo; Dr. Miguel de Vega (Chief Scientist), Ph.D. and author of 30+ patents in data optimization; Conrad Whelan (Founding CTO), founding Engineer at Uber; Mark McDermott (COO), former Innovation Lead at Nike; and Andrew Yeoh (CMO), early Hedera SVP Partner and former UBS and Rothschild Banker, among others.
Since its inception, the team has raised $50 million from investors, including Hack VC, Hashkey Capital, Distributed Global, and Maelstrom, through its private funding rounds.
TechnologyNillion Network is a decentralized infrastructure designed to support secure, privacy-preserving operations on high value data. It consists of two core layers: (i) the Coordination Layer, which manages governance and payments, and (ii) the Petnet, which handles computation and storage. Nillion’s Multi-Party Computation (MPC) protocol is central to the network’s functionality, enabling private data computations without revealing individual inputs. Nillion’s ecosystem is supported by a suite of application tools (i.e., nilAI, nilVM, nilDB, and nilChain) that empower developers to build privacy-focused applications. Academic research papers in cryptography and privacy technologies validate Nillion’s technology.
Nillion Network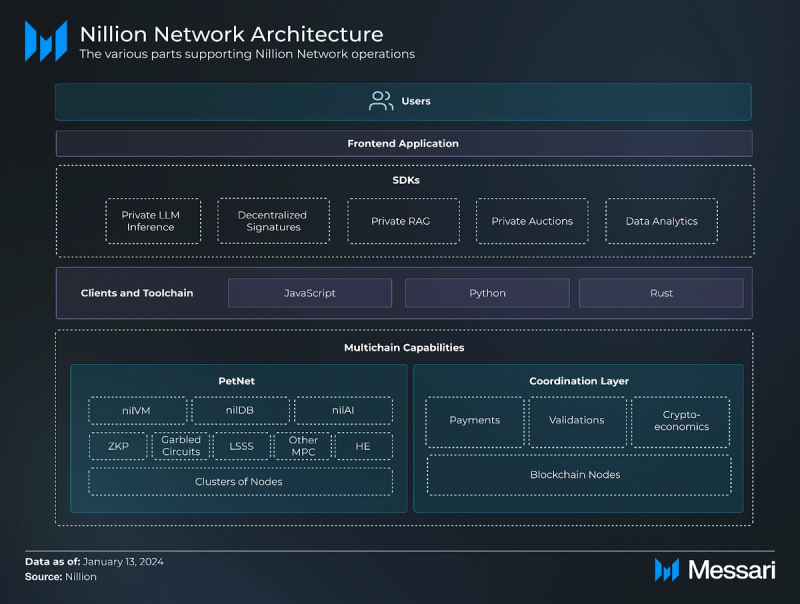
Nillion Network is a decentralized infrastructure designed to support private, high value data storage and computation. Scalability is achieved through clustering, which configures groups of nodes to meet specific performance, security, and cost requirements. Unlike traditional blockchains, the network operates without relying on a global shared state, enabling vertical scalability (by upgrading individual nodes or clusters) and horizontal scalability (by adding new nodes or clusters) to distribute workloads efficiently. Below is how each layer (i.e., Coordination Layer and Petnet) contributes to the network's architecture.
Coordination LayerNillion Network’s Coordination Layer, referred to as nilChain, is responsible for (i) managing rewards, (ii) payments, (iii) crypto-economic security, and (iv) inter-cluster coordination for the network.
Specifically, it coordinates payments for storage operations and blind computations performed on the network without handling the computations directly. Built with the Cosmos SDK, the Coordination Layer supports IBC for interoperability; however, it does not currently support smart contract execution, given the network’s core focus on storage and computation. While directly accessible via Keplr or Leap wallets, applications built on partner blockchains – explored further in the Key Projects section – will be fully abstracted. The nilChain has been running on testnet since June 2024.
PetnetThe Petnet (Orchestration Layer) is designed to integrate cryptographic technologies such as Multi-Party Computation (MPC), Fully Homomorphic Encryption (FHE), and Zero-Knowledge Proofs (ZKPs) to enable privacy-preserving computations and data management. This integration is achieved through two key components: (i) the compiler and (ii) the computing network. Specifically, the compiler simplifies the use of Privacy-Enhancing Technologies (PETs) by offering varying levels of abstraction while the computing network executes secure computations and manages encrypted data.
This approach is being implemented across Nillion Network via its Nada language compiler and the nilVM, with elements of all four abstraction levels already in development. The four levels of abstraction are as follows:
- Each PET protocol operates independently within its own Blind Module - similar to an isolated black box. There is no built-in unified interface or abstraction, and all orchestration happens on the client side; thus, developers can use the APIs to perform specific tasks, but cannot integrate or customize them.
- Various Blind Modules are integrated within each SDK, providing developers with a straightforward and unified way to manage multiple PET protocols without the need for cryptographic expertise. While the modules are not yet fully optimized, as they currently rely on a single PET protocol – a seamless, ready-to-use combination of PET protocols is already available.
- Blind Modules begin to support multiple PET protocols within a single Blind Module. This provides developers with the ability to choose from various trade-offs between performance and security - further simplifying cryptographic decisions for developers with minimal expertise.
- Blind Modules are deployed across loosely independent networks, called Clusters, which are managed by the NilChain. As the Nillion Blind Computer matures, the same Blind Module can be replicated across multiple Clusters, each with a distinct configuration. These configurations differ based on various factors (e.g., number of nodes, their locations, reputations, hardware specifications, security thresholds). This versatility allows developers to utilize the same functionality across different Cluster setups, allowing solutions tailored to specific needs (i.e., security, cost, hardware, regulatory compliance, etc).
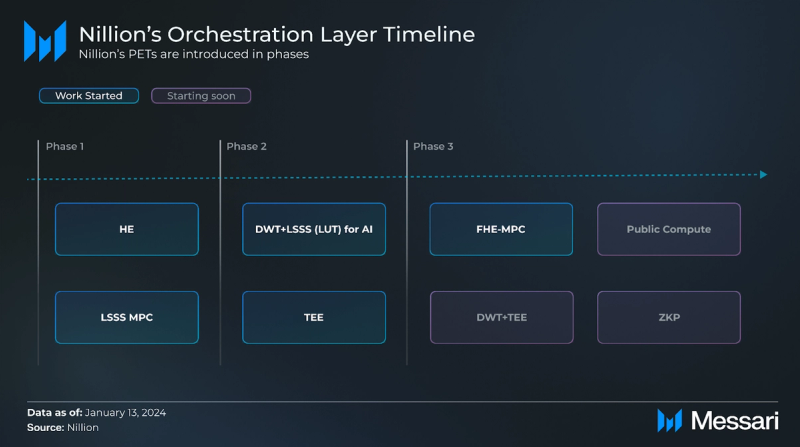
Nillion’s PETs are introduced in phases – each progressing through the four levels of abstraction as outlined above. Phase 1 (i.e., HE, LSSS MPC) and Phase 2 (i.e., DWT+LSSS, TEE) are further along the abstraction process and are already being integrated into Nillion Network. Among the technologies in Phase 3 (i.e., FHE-MPC, DWT+TEE, Public Compute, ZKP), FHE-MPC has begun advancing through the abstraction levels.
How It WorksHere is a detailed breakdown of how the components of Nillion Network operate:
- A user/developer interacts with a frontend application built using the JavaScript or Python client to submit data for storage or initiate blind computation requests.
- Applications using the JavaScript client interact with the Petnet for secure computations and encrypted data management. In contrast, Python client-based applications interact with the Coordination Layer for payments, routing, and multichain communication.
- The Coordination Layer processes payments using the appropriate blockchain's native gas token or NIL tokens.
- After the Coordination Layer processes the request, it forwards computational tasks to the Petnet, which houses PETs.
- The Petnet processes data by using PETs likeLinear Secret Sharing Schemes, Garbled Circuits, and/or Homomorphic Encryption, depending on the task's requirements.
- These computations are performed across a cluster of nodes.
- Each node in the Petnet manages only a fragment of the encrypted data (share).
- The nodes perform the assigned computations (e.g., addition, multiplication, or secure comparisons) on masked data and generate partial outputs.
- The Petnet aggregates these partial outputs to produce the final computation result securely and privately.
- The final result is routed back as follows:
- If using the JavaScript client, Petnet sends the result directly to the application for the user/developer to access.
- If using the Python client, the Coordination Layer retrieves the result from the Petnet and routes it to the application or relevant blockchain for further use.
- For blockchain-integrated use cases, the Coordination Layer delivers the result to the originating smart contract or decentralized application, allowing multichain functionality without requiring users to download new wallets.
Multi-Party Computation (MPC) is a subfield of cryptography that allows individuals to collaboratively compute a result from their combined data without revealing their inputs. Nillion has developed an MPC protocol called Curl, which is based on Linear Secret-Sharing Schemes (LSSS) but extends their capabilities to efficiently handle complex operations, such as divisions, square roots, trigonometric functions, and logarithms. This makes Curl highly scalable and ideal for real-world problems, such as privacy-preserving AI agents, where outputs do not scale linearly with inputs. Curl follows a structured two-phase workflow:
- Phase 1 (pre-processing to create shares): This phase generates and distributes shares of randomness to participants (computation entities) before processing the actual data using MPC techniques. Notably, the pre-processing phase operates independently of input values, relying only on the number of inputs to create the appropriate number of shares before computation occurs. It can be considered an abstraction layer – creating placeholders in advance that will later combine with the actual input data provided by users during Phase 2.
- Phase 2 (efficient computation of complex operations): The computation phase involves performing actual calculations on private inputs through three stages: (i) input, (ii) evaluation, and (iii) output.
- Input: Parties distribute shares of their inputs to the participants, ensuring information-theoretic security (ITS). Each participant receives one share per input value, maintaining confidentiality throughout the process.
- Evaluation: Parties efficiently compute complex operations on input shares using Nillion’s Curl protocol.
- Output: Local computation results are revealed and aggregated to produce the final outcome.
To learn more about Nillion’s implementation of MPC, read the original academic paper here.
Application ToolsBuilding on the foundation of Nillion Network, the application tools (i.e., nilVM, nilDB, nilAI, and nada integrated packages) provide developers with modular frameworks and utilities to quickly build privacy-preserving, high value data applications.
nilAInilAI is Nillion's suite of AI-focused privacy technologies (i.e., AIVM, nada-AI, and nilTEE). Here is how each works:
- AI Virtual Machine (AIVM): A secure AI inference platform built on Nillion’s MPC technology and Meta’s CrypTen framework. It uses Discrete Wavelet Transform (DWT), co-developed with Meta’s AI Research team, to accelerate inference. AIVM ensures private deep-learning model inference and deployment by keeping individual nodes blind to user prompts and model outputs, maintaining data confidentiality.
- nada-AI: A library for nilVM designed for AI applications, offering a PyTorch-like interface for running small models (e.g., Neural Networks (NN), Convolutional Neural Networks (CNN), Linear Regression, among others). Developers can also quickly bootstrap their projects using provided Google Colab notebooks.
- nilTEE: A solution that uses Trusted Execution Environments (TEEs) to run large language models (LLMs) during inference with high performance. Nillion recommends restricting TEE use to inference time rather than long-term data storage. Research is underway to enhance nilTEE and AIVM through split inference setups, further improving security and performance.
nilVM is a virtual machine that allows developers to create programs using PETs. Programs are written in Nada, Nillion’s open-source Python-based DSL, and developed using the Nillion SDK. Nada also includes libraries such as nada-ai (similar to PyTorch and scikit-learn), nada-numpy, nada-data, and nada-test to simplify program development. Developers can integrate nilVM into their applications using Python, Typescript, or CLI clients and leverage Storage APIs for secure data storage and retrieval on Nillion Network. Examples include a federated learning program, community-developed projects, and interactive demo use cases.
nilDB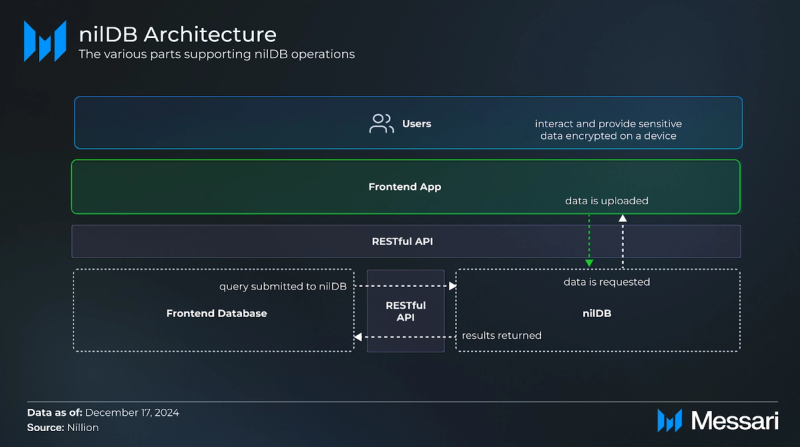
nilDB is an encrypted, distributed NoSQL database designed for privacy-preserving data storage and computation. Unlike regular NoSQL databases, nilDB eliminates reliance on a central authority by distributing encrypted data as secret shares across multiple nodes. Additionally, data owners can grant others access to run SQL-like queries, calculations, and privacy-preserving aggregations on the stored data.
Here is how it operates:
- Users encrypt their sensitive data locally on their devices.
- Users securely upload their encrypted data through the frontend application built on Nillion. The application securely uploads the encrypted data to nilDB via an integrated backend RESTful API.
- Encrypted data is split into secret shares using Nillion’s MPC protocol and distributed across a cluster of nodes in the nilDB network. Notably, no single node holds the complete dataset.
- Users provide explicit consent for specific data uses or queries, which can be withdrawn anytime through the application.
- Permissioned entities (e.g., companies or third parties) submit SQL-like query requests (e.g., lookups, range filters, or aggregate computations) through Nillion’s RESTful API.
- The nodes in the nilDB cluster collaboratively perform computations on the encrypted data without exposing sensitive information.
- Query results, such as averages, sums, or filtered datasets, are generated while maintaining data confidentiality.
- Only the final query result is returned to the requesting User via the RESTful API.
More information regarding the technical architecture can be read here.
Nada Integrated PackagesThe Nada language includes a variety of integrated packages, including nada-AI (previously discussed), nada-numpy, and nada-test with the following use cases:
- nada-numpy: A constrained adaptation of NumPy tailored for the Nada DSL. Compared to regular NumPy, nada-numpy allows efficient manipulation of array structures with strong typing requirements for data types, ensuring compatibility with MPC's strongly typed nature.
- nada-test: A testing framework for Nada programs that supports dynamic test generation at runtime. Developers can write test cases using Python, integrate the framework into pytest workflows, and define flexible input and output specifications.
Other tools (e.g., Nada DSL, Nada Sandbox, etc.) and the SDK can be explored on GitHub.
Research PapersNillion’s project team, in collaboration with multiple researchers, has published eight papers detailing various aspects of the protocol and its applications.
- Nillion: A Secure Processing Layer for Web3: Original vision paper outlining the potential possibilities for Nillion and its applications in decentralized ecosystems.
- Evaluation of Arithmetic Sum-of-Products Expressions in Linear Secret Sharing Schemes with a Non-Interactive Computation Phase: Explores Nillion’s MPC protocol for secure and efficient non-linear computations.
- Curl: Private LLMs through Wavelet-Encoded Look-Up Tables: Proposes Curl, a privacy-preserving inference framework for LLMs that leverages wavelet-encoded look-up tables to reduce communication overhead and improve efficiency.
- Technical Report on Secure Truncation with Applications to LLM Quantization: Explores secure truncation techniques in Linear Secret Sharing Scheme (LSSS)-based MPC environments for optimizing computations in LLMs.
- More efficient comparison protocols for MPC: Enhances the efficiency of secure comparisons in LSSS-based MPC systems.
- Technical Report on Threshold ECDSA in the Preprocessing Setup: Details preprocessing methods for threshold ECDSA, a distributed cryptographic system that securely manages and uses private keys across multiple parties.
- Technical Report on Decentralized Multifactor Authentication: Introduces decentralized frameworks for improving secure authentication processes.
- Ripple: Accelerating Programmable Bootstraps for FHE with Wavelet Approximations: Describes Ripple, a framework that uses Discrete Wavelet Transforms (DWTs) to compress lookup tables, reducing the computational cost of bootstrapping in Fully Homomorphic Encryption (FHE).
The NIL token will serve several functions within the network, including:
- Paying for computational services, data storage, AI inference, and transaction fees across the Petnet and Coordination layers. Specifically, developers use NIL to access Nillion’s privacy-preserving computation services for their applications.
- Staking and supporting network security and earning rewards.
- Validators bond NIL to validate transactions and computations, securing the Coordination Layer.
- Petnet nodes stake NIL to increase their cluster’s security and attract developers and applications.
- Participating in decentralized governance, proposing and voting on various network decisions (i.e., protocol upgrades, resource allocation, and community grant initiatives).
Governance decisions are conducted through an onchain voting mechanism. Specifically, any NIL tokenholder can propose changes to the network provided they meet the minimum token deposit requirements. Proposals can also be submitted by community committees or working groups established through prior governance actions.
Voting rights extend to key decisions such as:
- Introducing new features or updates.
- Allocating rewards pools for grants, developer incentives, and community-driven projects.
- Adjusting network pricing, validator requirements, or delegation limits.
- Modifying governance structures like quorum requirements or proposal thresholds.
- Expanding interoperability, forming strategic partnerships, or implementing transparency and auditing mechanisms.
Voting power is proportional to the amount of NIL staked, where stakers delegate their voting powers to validators while retaining the ability to vote on proposals themselves.
State of the Nillion Ecosystem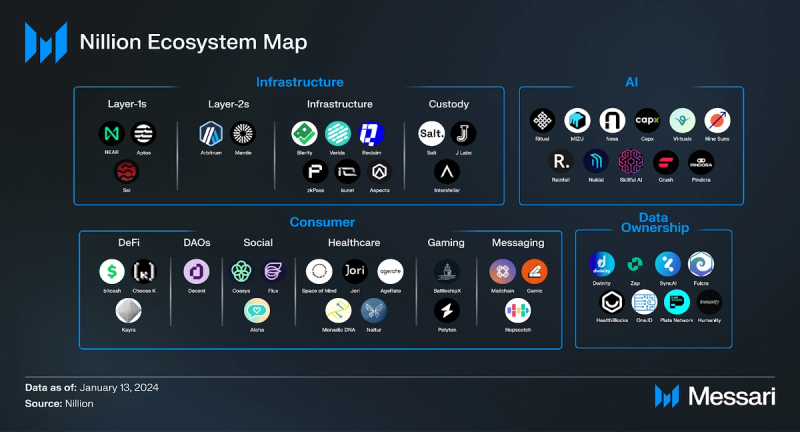 Key Sectors
Key SectorsKey sectors that highlight the variety of benefits Nillion provides include:
- Artificial Intelligence: Nillion processes data and inference without exposing sensitive information, bridging the gap between secure local AI processing and the scalability of centralized non-private AI systems.
- Personalized Agents: AI agents can store, compute, and handle private data.
- Private Model Inference: AI models can process private data securely, minimizing the risk of exposure to third parties and enabling private LLMs.
- Private Knowledge Bases and Search: Data can be stored in encrypted form while still enabling search functions for AI agents and other AI use cases.
- Data Ownership: Nillion’s cryptographic infrastructure supports secure data marketplaces by allowing users to control and sell their data to buyers.
- Blockchains: Nillion allows blockchain applications to send blind storage and compute requests to Nillion Network, complementing blockchains' public data features. It also supports onchain settlement by allowing applications to decrypt relevant data on the blockchain.
- Healthcare: Nillion supports privacy-preserving analysis of healthcare data across institutions and users.
- DePIN: Integrating with Nillion, DePIN projects can securely store and process sensitive operational data.
Key projects that highlight the variety of benefits Nillion provides include:
- Virtuals Protocol: An AI agent co-ownership platform that developed a multimodal AI agent library and, by using Nillion, allows private training and inference of its AI models to build personalized AI agents.
- Aptos/NEAR/Arbitrum/Sei: Layer-1 and Layer-2 blockchains that integrated blind data storage and computation to enhance data handling within smart contracts.
- Ritual: An AI platform building a decentralized AI inference network, integrating Nillion in its backend for private inference.
- Zap: A data platform aggregating user data into Decentralized Data Pools within Nillion, offering secure insights through blind computation and Zero-Knowledge Transport Layer Security (zkTLS).
- Reclaim Protocol: A zkTLS infrastructure platform that allows users to prove identity and reputation through offchain platforms trustlessly and uses Nillion as a storage and processing platform for the proofs generated.
- Healthblocks: A fitness application that uses Nillion to maintain user ownership and control of data while allowing third-party insights without exposing individual details.
- MonadicDNA: A genomics platform that uses Nillion to keep data encrypted throughout its lifecycle, providing an alternative to centralized providers (e.g., 23andMe).
Launched in January 2024, the Nucleus Builders Program supports developers in creating decentralized, privacy-preserving applications with Nillion’s technology. Participants gain access to (i) the Nillion SDK, (ii) development tools (e.g., nilVM, nilDB, and nilAI), and (iii) funding and technical resources to accelerate overall development. Since its inception, Nucleus has attracted nearly 50 participants across over ten verticals, with ecosystem projects collectively raising $100+ million.
Network MetricsThe Nillion Verifier Program, announced on Aug. 27, 2024, allowed participants to support the network's integrity and functionality by either (i) uploading "Secrets," which are fragmented pieces of sensitive data across various categories, or (ii) setting up a verifier to challenge secrets and secure the network, ensuring network data shares remain reliable and intact.
Participation in the Verifier program closed on Dec. 11, 2024, and reached ~500,000 verifiers actively contributing to the network, collectively processing ~195 million secrets and securing ~1,050 GB of data. The real-time verifier dashboard can be found here.
RoadmapReleased on May 31, 2024, the Nillion roadmap has four key phases:
- Phase 1 - Genesis Sprint (Completed Phase): This phase established (i) the foundational Coordination Layer during the testnet launch, (ii) tested core functionalities such as Keplr wallet creation, token transfers, staking, and governance, (iii) provided developers access to the Nillion SDK with telemetry capabilities for early application development, and (iv) conducted load testing to evaluate transaction throughput and network scalability.
- Phase 2 - Catalyst Convergence (Ongoing Phase): This phase (i) integrates the Petnet with the Coordination Layer, (ii) onboards external nodes to progress toward complete decentralization, (iii) introduces Blind Applications for secure data processing, and (iv) supports cross-chain functionality, expanding Nillion into a multichain ecosystem.
- Phase 3 - Hardening: This phase will (i) include the mainnet launch and Token Generation Event (TGE), (ii) operationalize external nodes, (iii) enable real-world interactions through Blind Computation, and (iv) validate the network’s previously built applications under live conditions.
- Phase 4 - The MultiCluster Future: This phase will (i) focus on horizontal scaling by adding clusters of public nodes, (ii) boost computational power, (iii) optimize the network for marketplace-specific applications, and (iv) is designed for scalability while maintaining security and privacy.
Nillion is a decentralized infrastructure designed to handle high value, privacy-sensitive data across various applications, from AI agents to private DeFi. Leveraging a combination of advanced PETs (e.g., MPC, FHE, TEE), Nillion expands the usability of decentralized networks and possibilities for decentralized applications. Nillion’s architecture – the Coordination Layer and Petnet – supports scalability through clustering while ensuring data confidentiality and decentralized trust.
The Nillion ecosystem continues to expand, marked by milestones such as (i) the Nucleus Builders Program, which supports ~50 projects across several verticals, and (ii) the participation of ~500,000 Verifiers who have collectively processed ~195 million secrets and secured ~1,050 GB of data. Partnerships with Virtuals, NEAR, Meta, and Aptos and ongoing roadmap developments toward the mainnet launch and multicluster scalability highlight Nillion’s progress in advancing privacy-focused data management and secure computation.
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.