and the distribution of digital products.
DM Television
The Quantum Threat: How Enterprises Can Safeguard Encryption Against Tomorrow's Tech
Quantum computing - a field marked by rapid advancement and increasing investment - has considerable potential in fields such as cryptography, material science, and complex system simulations. Yet, the emergence of quantum computing represents a profound challenge to the security of contemporary encryption methods.
\ This technology makes it necessary for organizations to adopt quantum-resistant cryptographic strategies, and to do so deliberately and proactively. The computational power of quantum computers threatens to render traditional encryption algorithms obsolete; thus a shift in cryptographic practices is needed. Consequently, organizations must implement new cryptographic standards and shore up their cybersecurity frameworks to defend against evolving quantum threats.
\ This article will discuss the ramifications of quantum computing on encryption and security and will offer prescriptive recommendations for organizational preparedness in anticipation of this technological evolution.
The Quantum Threat to EncryptionCurrent encryption protocols, such as RSA and Elliptic Curve Cryptography (ECC), are predicated on the computational infeasibility of factoring large integers or solving discrete logarithm problems. True, these problems are practically insurmountable for classical computers; however, they can be efficiently resolved by a sufficiently powerful quantum computer employing Shor's algorithm.[1] Thus, quantum computers can compromise the encryption mechanisms that currently safeguard online communications, financial transactions, and confidential data repositories.
\ There are many consequences of this threat that must be considered. The absence of secure encryption mechanisms would render all information transmitted over public networks, which would encompass both historical and future communications, susceptible to interception and decryption.[2] In addition, the integrity and authenticity of transmitted data would be jeopardized, and would permit undetectable tampering. Such vulnerabilities would contravene regulatory mandates for data privacy and security, and would engender significant legal and ethical ramifications.
Why Quantum-Resistant Cryptography is Non-NegotiableTo mitigate the quantum threat, researchers and organizations are intensively developing quantum-resistant cryptographic algorithms, collectively termed post-quantum cryptography (PQC).[3] These algorithms are engineered to withstand attacks from both classical and quantum computers in order to ensure the confidentiality and integrity of information as quantum computing becomes more widespread. The formulation and standardization of PQC algorithms are imperative for safeguarding various sectors, including governmental and military communications, financial transactions, healthcare data, personal data storage, and corporate networks.[2] Nevertheless, the transition to PQC is a multifaceted and protracted endeavor, and demands substantial contributions from the global technological community.
NIST PQC StandardizationThe National Institute of Standards and Technology (NIST) is standardizing post-quantum cryptographic algorithms to protect against the severe threat of quantum computers to cryptographic standards. The organization is standardizing two types of algorithms:
Key Encapsulation Mechanisms (KEMs)Key Encapsulation Mechanism (KEM) is a set of algorithms that establish a shared secret key between two parties over an insecure channel. The KEM algorithm selected for standardization is CRYSTALS-KYBER, a lattice-based KEM chosen for its strong security and excellent software, hardware, and hybrid settings performance.
\
Digital Signature AlgorithmsDigital Signature Algorithms are cryptographic algorithms used to generate and verify digital signatures, which provide authentication and data integrity. CRYSTALS-Dilithium algorithm - a lattice-based digital signature algorithm is selected by NIST for standardization.
\
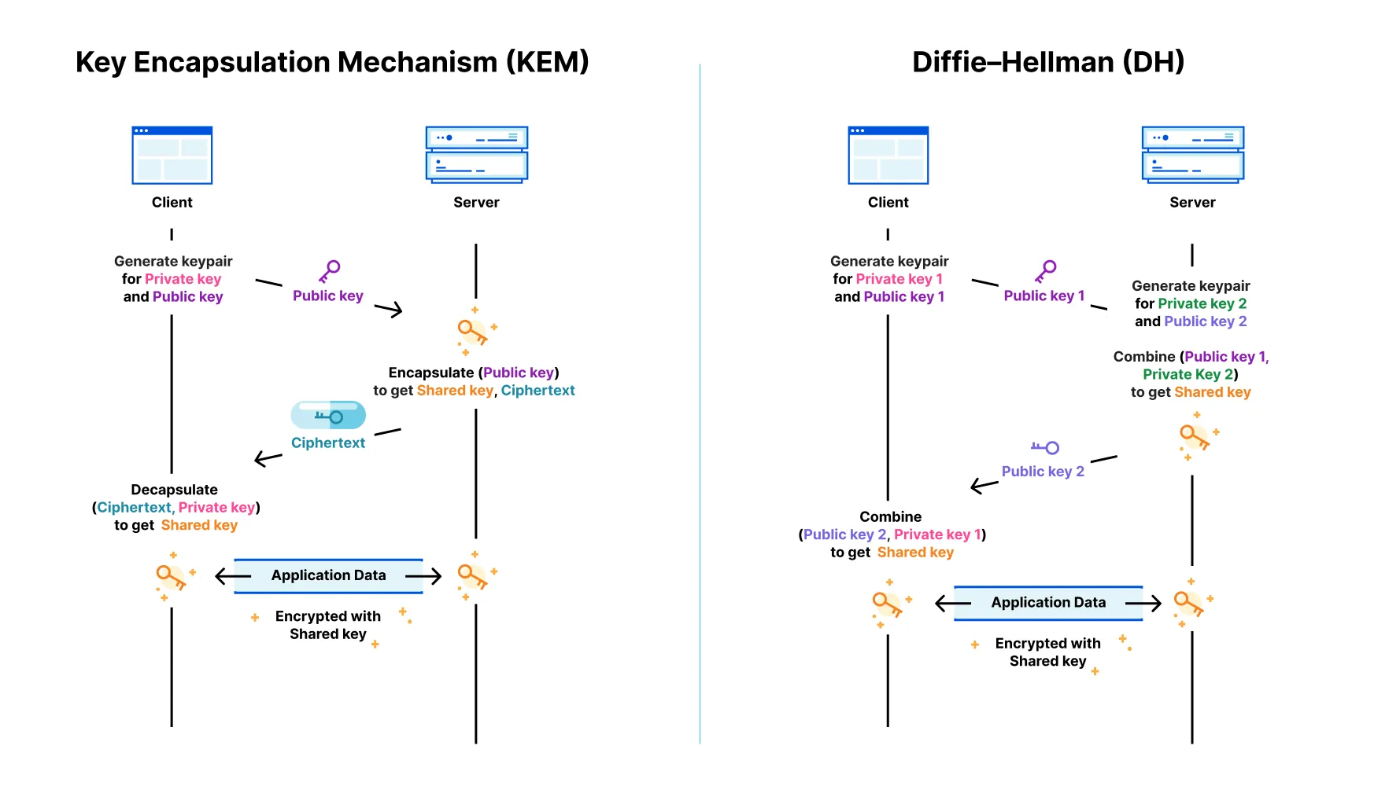
\ \ KEM vs Diffie-Hellman — Cloudfare
Strategies for Adopting Quantum-Resistant CryptographyOrganizations must adopt a strategic approach to implementing quantum-resistant cryptography to counter the risks posed by quantum computing. The following recommendations are proposed:
\
Assess Quantum Risk Organizations should undertake a thorough evaluation of their existing encryption systems to identify vulnerabilities to quantum attacks. This evaluation should consider the sensitivity and longevity of the data being protected and the potential impact of a security breach.[2]
\
Develop a Transition Plan Based on the risk assessment, organizations should formulate a comprehensive plan for transitioning to quantum-resistant cryptography. This plan should delineate timelines, resource allocation, and methodologies for integrating PQC algorithms into existing systems and protocols.[2]
\
Engage in Standardization Efforts Organizations should actively engage in the standardization initiatives for PQC algorithms, such as those orchestrated by the National Institute of Standards and Technology (NIST) and the European Telecommunications Standards Institute (ETSI).[2][3] Participation in these efforts ensures that organizational requirements and use cases are incorporated, and that the resulting standards fulfill their security needs.
\
Implement Hybrid Cryptography As an interim measure, organizations can deploy hybrid cryptographic solutions that amalgamate traditional encryption methods with PQC algorithms.[2] This approach affords protection against both classical and quantum threats, facilitating a gradual transition to fully quantum-resistant systems.
\
Promote Collaboration and Knowledge Sharing The adoption of quantum-resistant cryptography necessitates collaboration and the dissemination of knowledge among organizations, researchers, and industry specialists. Organizations should actively participate in conferences, workshops, and forums to remain abreast of the latest advancements and best practices in PQC.[3]
With all this to consider, it is also important to remember that quantum computing represents a notable advancement in computational power, with its potential to solve complex problems far beyond the reach of classical computers. According to a report by IBM, quantum computers are expected to achieve "quantum advantage" by 2025; this means that they will outperform the most powerful classical supercomputers in specific tasks [6]. Additionally, a study by Market Research Future projects that the quantum computing market will grow at a compound annual growth rate (CAGR) of 34.3%, and will reach a market size of approximately $2.2 billion by 2026 [7]. The prospective capability of quantum computing to compromise current encryption methods constitutes a formidable challenge that organizations must address with foresight. Organizations can uphold the security and privacy of their data amidst this technological upheaval by adopting quantum-resistant cryptography and engaging in standardization efforts. Collaboration, risk assessment, and meticulous planning are critical to achieving a successful transition to a quantum-secure future.[2][3]
References- Quantum Computing Impact on Cybersecurity
- ETSI Quantum-Safe Cryptography
- The Quantum Insider - Quantum Security
- Scientific American - Are Quantum Computers About to Break Online Privacy?
- Wikipedia - Post-Quantum Cryptography
- IBM. (2020). The Quantum Decade.
- Market Research Future. (2021). Quantum Computing Market Research Report.
\ \
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.