and the distribution of digital products.
DM Television
Lumoz Unveils TEE+ZK Multi-Proof for On-chain AI Agent
With the development of Web3, decentralized AI Agents have emerged as a key application. These agents operate autonomously without relying on centralized servers, handling user data and interacting with blockchain smart contracts. However, the openness and trustless nature of Web3 pose significant security challenges.
\ AI Agents demonstrate potential in Web3 applications, such as managing private keys, automating transactions, and supporting DAO operations. Yet, their shortcomings in trustworthiness and accountability deviate from core principles like decentralization and transparency. This limits their broader adoption and hinders future development.
Current StateAt present, most AI agents operate in untrusted environments, facing numerous challenges in terms of security and transparency. These agents often handle sensitive user data and perform critical tasks, yet their operating environments lack the necessary safeguards. This exposes them to risks such as data leaks, tampering with execution logic, or unverifiable computation results. Commonly assumed issues include:
- The agent's initialization process is untampered.
- Data provided by external APIs is secure and reliable.
- Private keys are properly managed and cannot be leaked.
- User input remains uncompromised during transmission.
By default, all worker nodes are considered untrusted. Malicious workers may attempt the following improper actions:
- Accessing sensitive user data.
\
- Providing incorrect computation results or failing to execute tasks entirely.
\
- Degrading service quality, such as reducing computational capacity or disrupting network connections.
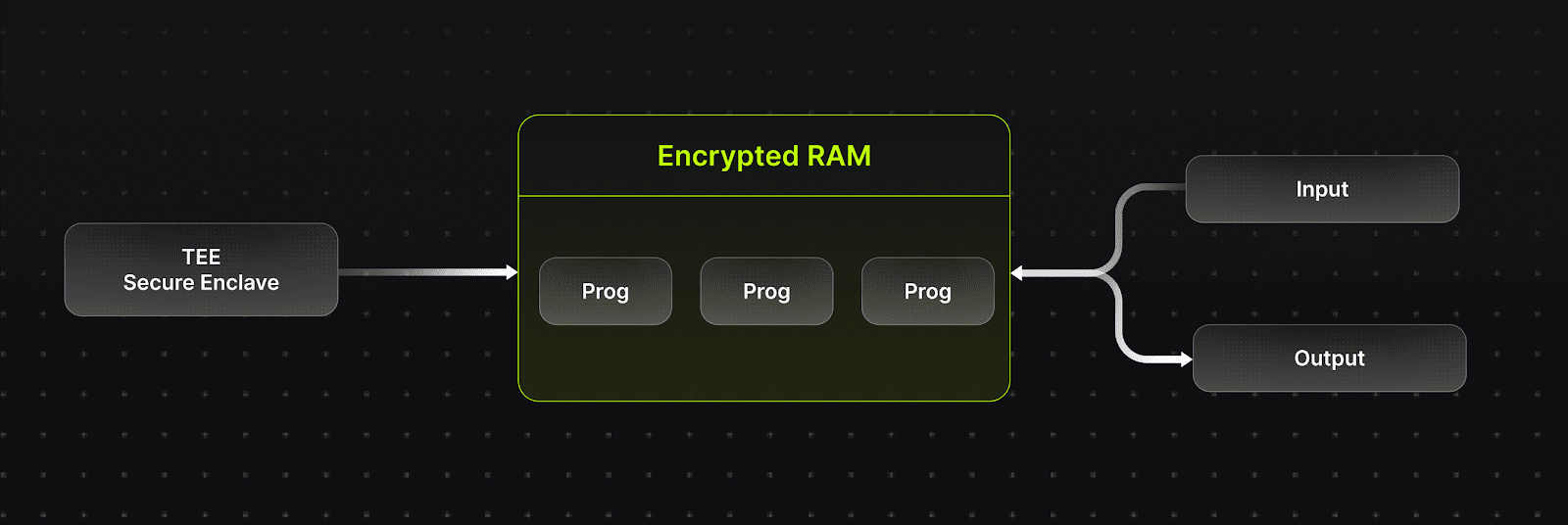
\ To ensure a trustless system, Lumoz leverages Secure Enclave (Trusted Execution Environment, similar to Intel SGX) and an innovative key management mechanism. Secure Enclave provides robust hardware security guarantees, including the following features:
\
- Data Confidentiality: All memory data is encrypted.
\
- Execution Integrity: Even if an attacker gains control of the operating system or physical device, the correctness of the execution process remains intact.
\
- Remote Attestation: Users can verify remotely that both hardware and software are operating within a secure environment.
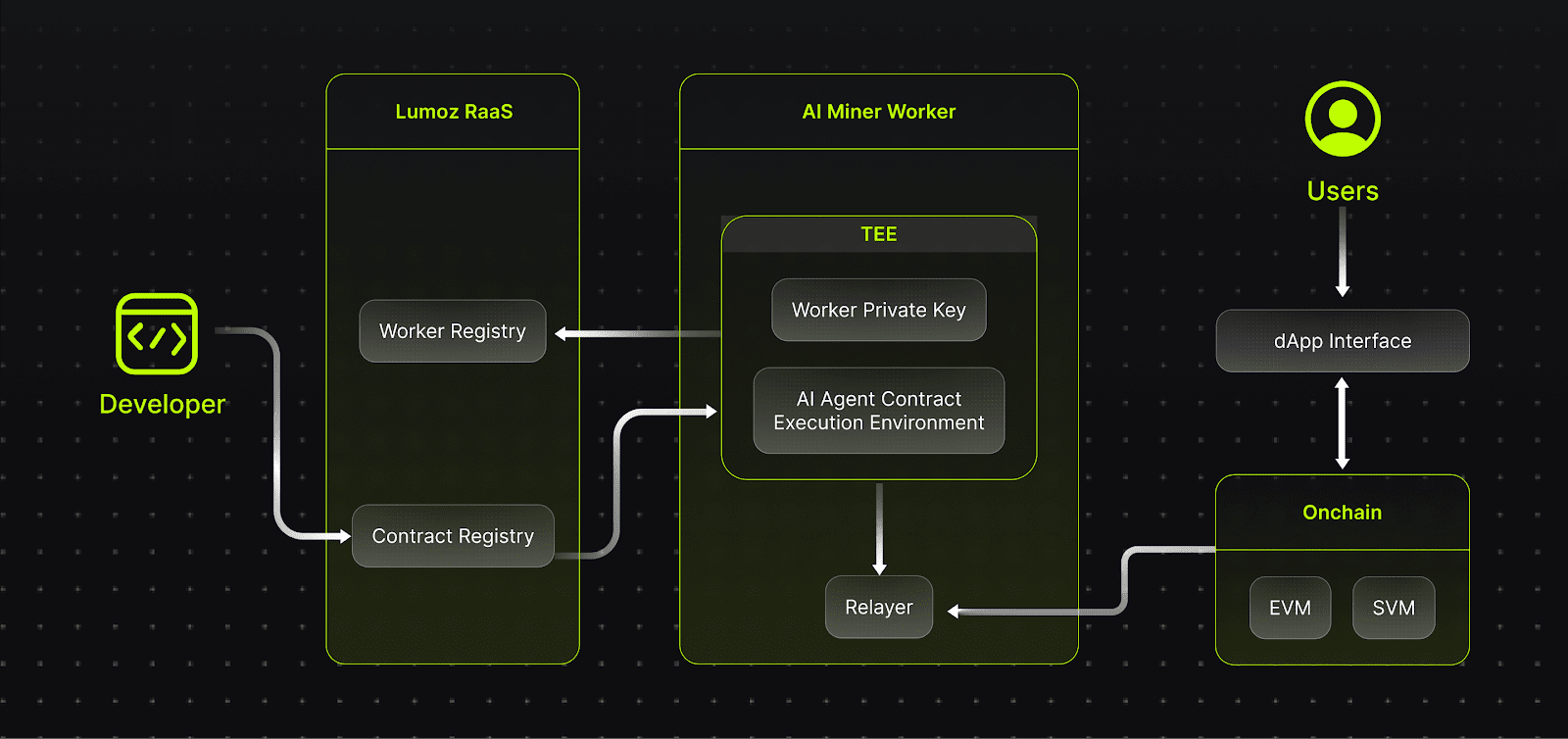
Lumoz aims to be the core processing platform for AI computation, playing a critical role in supporting scalable blockchain infrastructure. By integrating Trusted Execution Environment (TEE) technology, Lumoz ensures the security and transparency of its computational processes.
\
This innovative combination merges the decentralization strengths of blockchain with the robust security of TEE, enabling Lumoz to deliver not only a decentralized cloud computing network but also the ability to efficiently execute various computational tasks in a trust-minimized environment. \n
- Hardware-Level Security: The secure hardware enclave ensures privacy, confidentiality, and data integrity.
\
- No Computational Overhead: Applications running in TEE operate at nearly the same speed as those in a standard CPU environment.
\
- Low Verification Costs: Verifying TEE proofs consumes minimal gas, requiring only ECDSA verification.
- Tamper-Proof Data: Ensures that user request/response data cannot be altered by intermediaries. This requires secure communication channels and robust encryption mechanisms.
\
- Secure Execution Environment: Both hardware and software must be protected from attacks, leveraging TEE to create an isolated environment for secure computation.
\
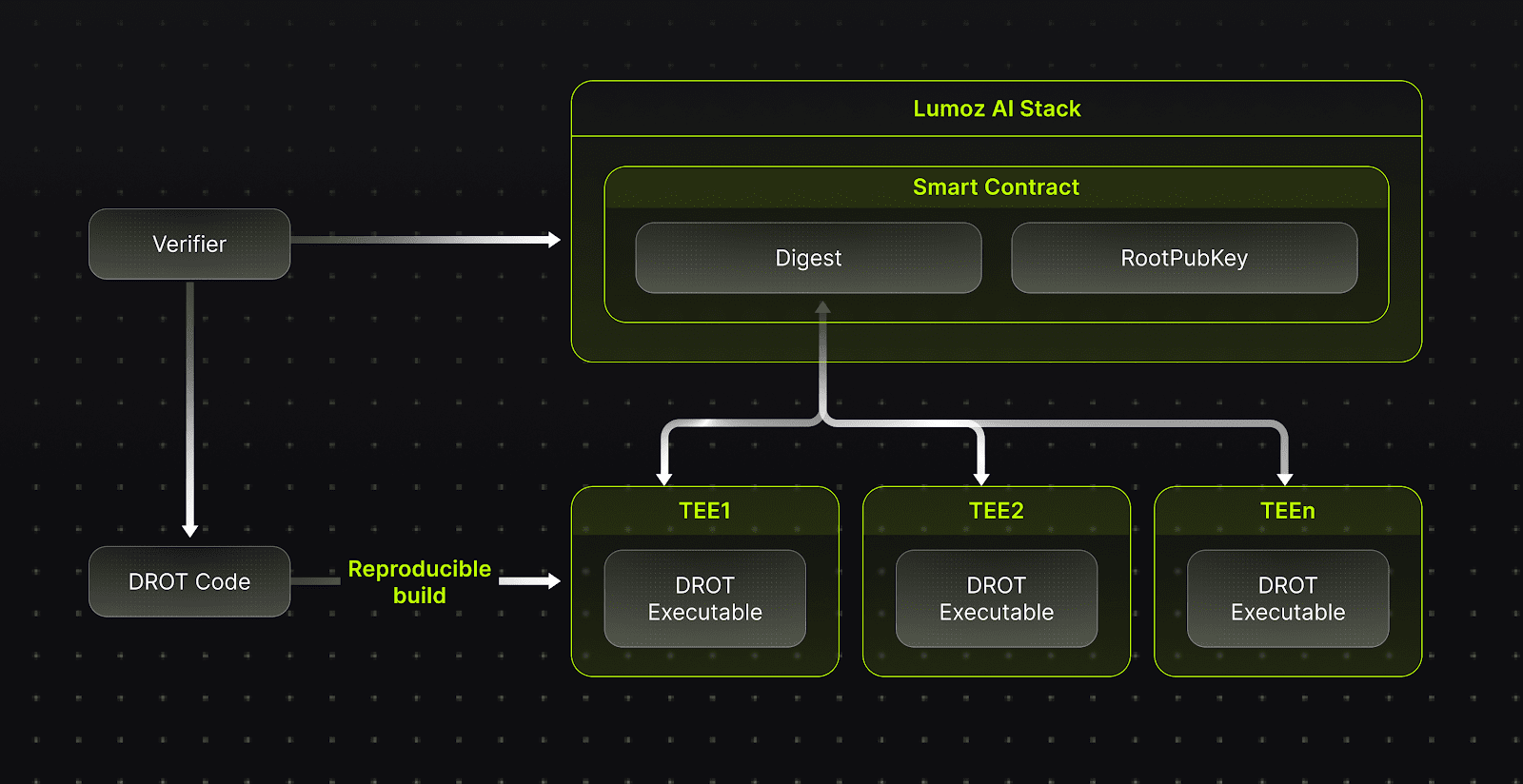
- Open-Source and Reproducible Versions: The entire software stack, from the operating system to application code, must be reproducible. This allows auditors to verify the system's integrity.
\
- Verifiable Execution Results: AI computation results must be verifiable to ensure that outputs are trustworthy and untampered.
 TEE Server Security Verification
TEE Server Security Verification
When the service starts, it generates a signing key within the TEE.
You can obtain CPU and GPU attestations to verify that the service is running within a confidential VM in TEE mode.
\
The attestation includes the public key of the signing key, proving that the key was generated within the TEE.
\
All inference results are signed using the signing key.
\
You can use the public key to verify that all inference results were generated within the TEE.
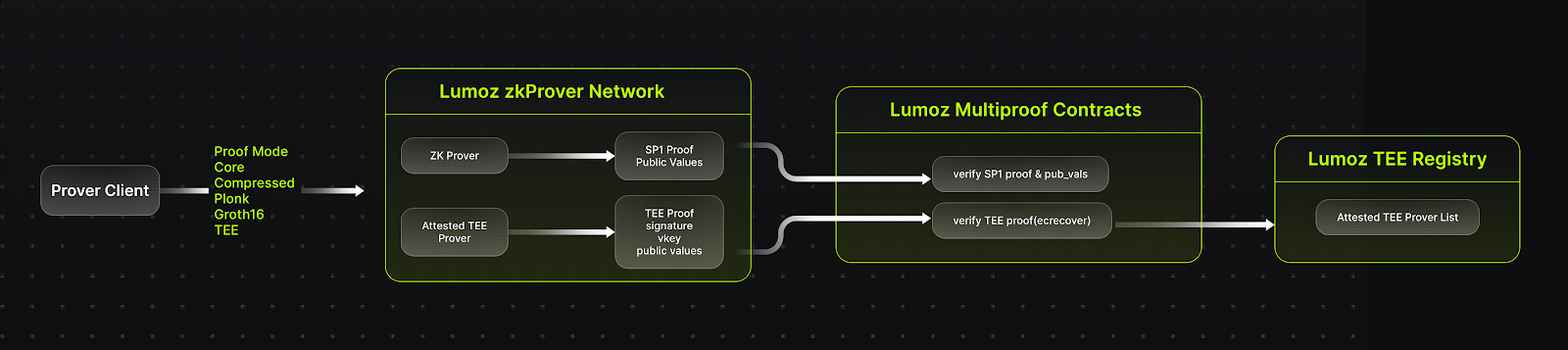
No single cryptographic system can be guaranteed to be 100% secure. While current Zero-Knowledge (ZK) solutions are theoretically secure, they cannot ensure flawless operation across the entire system, especially from an engineering perspective, given the complexity of ZK implementations.
\
This is where multi-proof systems come into play. To mitigate potential errors in ZK implementations, hardware-based solutions like Trusted Execution Environments (TEE) can act as a dual-factor verifier, providing an additional layer of security for ZK-based projects such as AI Agents.
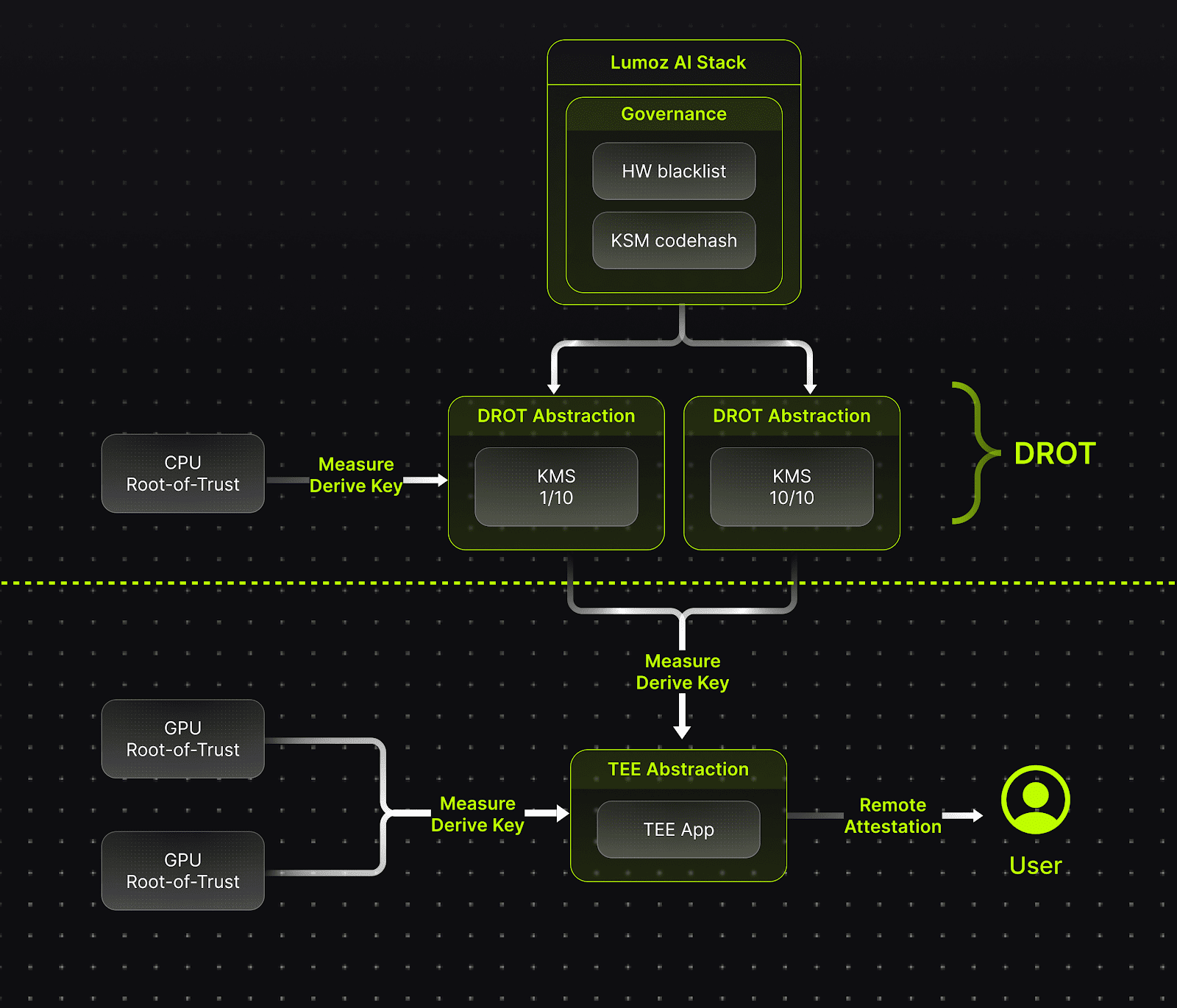
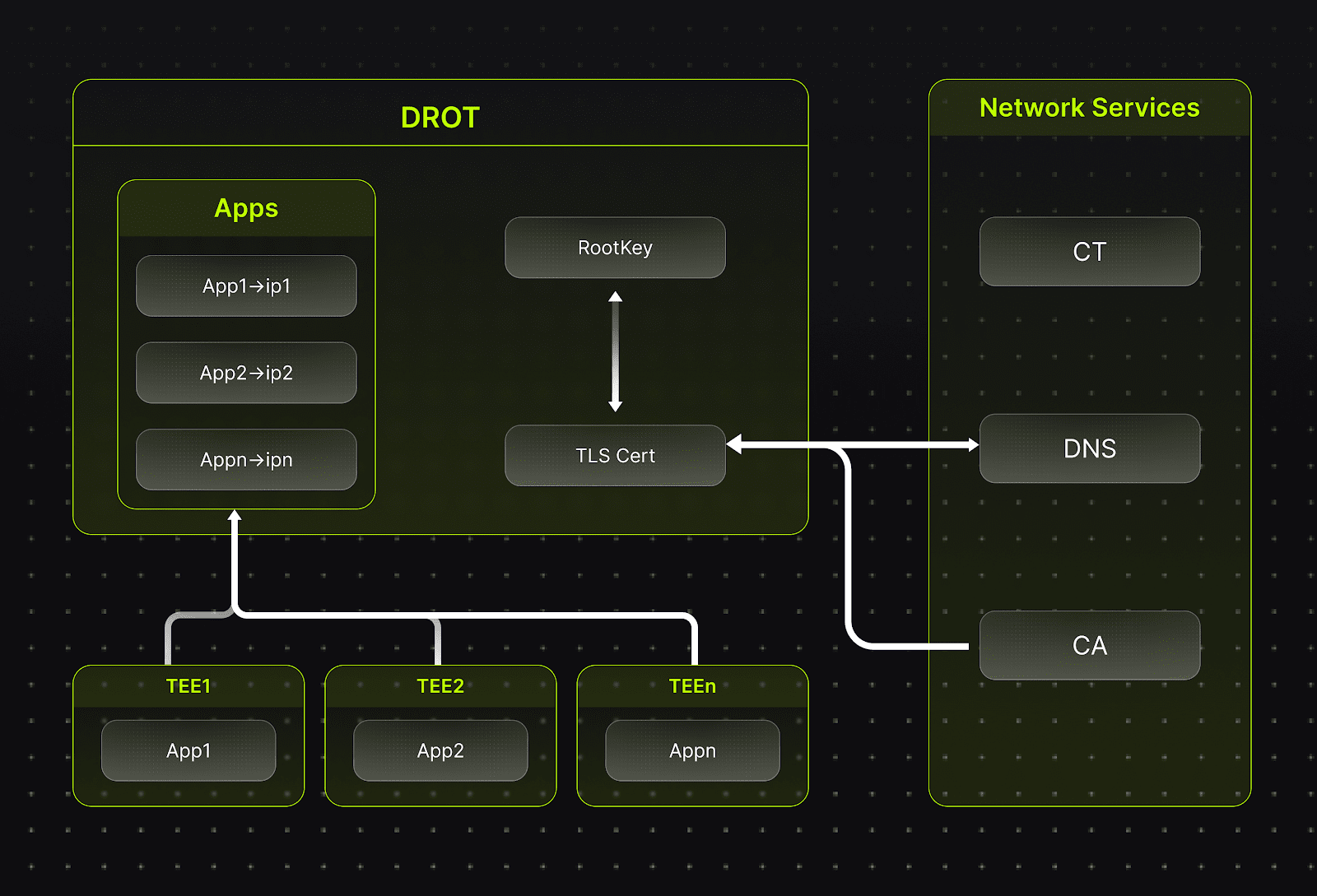
Decentralized Root-of-Trust (DROT) is a core component of the Trusted Execution Environment (TEE) trust chain. Ultimately, user verification relies on remote proofs signed by the CPU, which depend on a set of hardware-stored keys for generation. The hardware components responsible for managing these root keys, verifying firmware and applications, and issuing remote proofs are collectively referred to as DROT. \n
In the overall design, key management follows the principle of least privilege, meaning that the secrets known by each entity are strictly limited to what is necessary to perform its specific task.
In the solution design, the certificate management module serves as a reverse proxy for applications running on the network. It is important to note that as part of the overall solution, it operates within the TEE and is managed by smart contracts.
The TEE and ZK multi-proof architecture provided by Lumoz combines Trusted Execution Environment (TEE) with Zero-Knowledge Proofs (ZK) to create a multi-layered security framework. This innovative solution addresses the safety, privacy, and verifiability challenges faced by most AI Agents in untrusted environments.
\ By integrating TEE's hardware isolation capabilities with ZK's cryptographic verification features, the technology effectively resolves issues related to data protection and execution transparency. This aligns with the core principles of decentralization and transparency inherent to Web3.
\ This architectural approach enhances the trustworthiness and usability of AI Agents, unlocking greater potential as technology continues to evolve and standardize.
\ For more updates, visit the Lumoz website (https://lumoz.org/) and social media (https://x.com/LumozOrg).
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright 2025, Central Coast Communications, Inc.