and the distribution of digital products.
How Remote Access Trojans Bypass Traditional Security Measures
Remote Access Trojans (RATs) have become a significant cybersecurity threat, frequently used by attackers to gain unauthorized control over victim systems. Unlike traditional malware, RATs provide attackers with full access to compromised devices, enabling them to steal data, manipulate systems, and conduct surveillance.
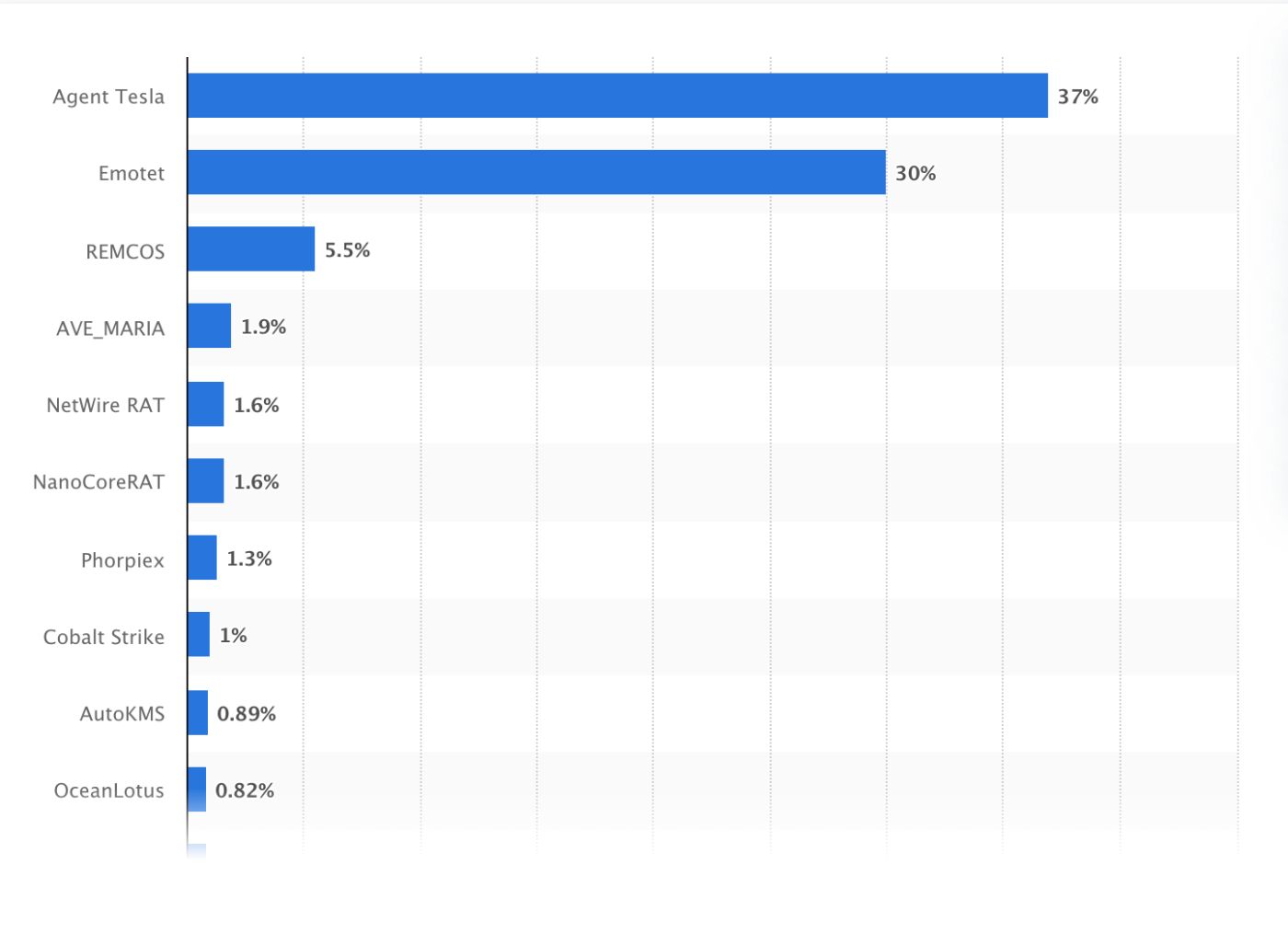
\ What makes RATs especially dangerous is their ability to bypass conventional security defenses like firewalls and antivirus software. In the first half of 2023, Agent Tesla emerged as the most prevalent RAT, responsible for nearly 37 percent of detections. Emotet followed with a 30 percent share, while REMCOS accounted for 5.5 percent.
\
These advanced trojans often leverage zero-day vulnerabilities, encryption, and stealth tactics to avoid detection. Recent studies reveal that RATs continue to evolve, emphasizing the urgent need for more sophisticated security measures to address this growing threat.
What Are Remote Access Trojans?A remote access trojan (RAT) is a malicious software designed to allow cybercriminals to control your device without you being aware. A RAT, once installed, allows the attacker to do a range of actions as if they were right in front of your computer, from opening files to tracking your activities and even activating your web camera/mic streaming.
Common Features of RATsRATs have a rich feature set for stealth and effectiveness:
\
- Stealth Operations — RATs are crafted to run silently in the background. They frequently pretend to be reputable software to avoid detection.
- Remote Control: This is where the attacker can control your system from a remote location. For example, running commands to download files or change settings without your permission.
\
- Data Exfiltration: Stealing sensitive information is one of the main functions RATs was created. That could be anything from passwords to your personal documents.
\
- Persistence: RATs are designed to be hidden and remain operational even after restarting your computer. They are the only ones who can make pain in the ass to reinstall, or they just resist removal.
\ Using periodic security updates and scans of your software can aid in remote access trojan removal, ensuring that your device remains secure from such malicious intrusions.
Traditional Security MeasuresAdvanced security solutions such as firewalls, antivirus software, and IDS are a must to prevent remote access Trojans.
\ A firewall is a gatekeeper, examining network traffic and staving off the unauthorized. Even though it might work, some advanced attacks may end up falling through the cracks.
\ Known malware is scanned for by the antivirus software. Failing which, if any RAT is detected, Antivirus solves to remove it. Yet new threats could bypass detection if the software is not kept up to date.
\ An Intrusion Detection System (IDS) constantly monitors your network for suspicious behavior and notifies you that unauthorized access has been attempted, such as a remote access trojan.
\ Although these tools provide some security, no one single approach is completely fail-safe. In order to protect your systems, combining multiple layers of security and staying alert is the key.
How RATs Bypass Traditional Security MeasuresLet’s explore how RATs bypass traditional security measures, making remote access trojan removal challenging.
\
- Exploiting Software Vulnerabilities
RATs often exploit unpatched software vulnerabilities in programs like browsers or operating systems. For instance, the CVE-2019-0708 vulnerability, also known as "BlueKeep," allowed RATs to infiltrate unpatched Windows systems.
\ Keeping your software updated is crucial for remote access trojan removal, as unpatched cybersecurity vulnerabilities are a primary way RATs slip past defenses.
\
- Social Engineering Techniques
Phishing and spear-phishing emails are common ways attackers deliver RATs. These emails trick you into clicking malicious links or downloading infected attachments, bypassing security if you fall for the trap.
\ Human error is often the weak link in security. Even with advanced security tools, if you unknowingly click on a malicious email, traditional security measures may not save you.
\
- Use of Encryption and Obfuscation
RATs use encryption to hide their activity from security systems. This encrypted traffic can slip past firewalls unnoticed. Additionally, code obfuscation makes it hard for traditional antivirus software to detect malicious code.
\ The ability of RATs to hide their presence using encryption makes remote access trojan removal even trickier, as the malware can operate stealthily for long periods.
\
- Living off the Land
Instead of installing new files, RATs often use existing system tools, such as PowerShell, to carry out attacks. This approach allows them to blend in with normal system activity, evading traditional security measures.
\ By using what’s already on your system, RATs blend in with normal operations, making it difficult to spot and remove them using conventional security software.
\
- Polymorphism and Metamorphism
RATs use polymorphic and metamorphic techniques to change their signatures, making them hard to detect with signature-based antivirus programs.
\ This adaptability makes remote access trojan removal challenging, as RATs can continuously evolve to evade detection.
Enhancing Security Against RATsThe first step in defending against RATs is enhancing your detection methods. Traditional antivirus software may not always catch these stealthy trojans. To improve your defense:
\
- Deploy advanced detection tools: Leverage behavior-based detection systems that analyze anomalies in your system. Unlike signature-based tools, these can catch RATs even when they use techniques like encryption or polymorphism to hide.
\
- Patch vulnerabilities regularly: Many RATs gain access by exploiting unpatched software vulnerabilities. Ensure that all your applications and operating systems are updated consistently to reduce the risk of exploitation.
\
- Use strong firewalls and network monitoring: Implement strong firewalls and monitor network traffic for suspicious activity, such as unusual outbound communications that may indicate RAT’s presence.
\ If you've already been hit, prioritizing remote access trojan removal with specialized malware removal tools is critical to eliminate the threat.
Best Practices for Cybersecurity Awareness and ResponseCybersecurity is a team effort. To protect yourself and your organization effectively, focus on closing the cybersecurity skills gap within your team. Here’s how:
\
- Invest in training: Educate your staff on the latest phishing and social engineering tactics used to spread RATs. Awareness reduces the chances of accidental downloads or clicking malicious links.
\
- Enforce strong access controls: Limit access to sensitive data and systems to only those who need it. Use multi-factor authentication to add an extra layer of security.
\
- Develop a response plan: Having a strong response plan in place ensures you’re prepared if a RAT does infiltrate your network. A well-designed plan should include steps for containment, remote access trojan removal, recovery, and future prevention.
Remote Access Trojans (RATs) are adept at bypassing traditional security measures through various methods like exploiting software vulnerabilities, using social engineering, and employing encryption and obfuscation. They also blend in with existing system tools and frequently change their code to evade detection.
To effectively counter these threats, it's essential to keep your software updated, be vigilant against phishing attacks, and use advanced security solutions that go beyond traditional defenses. Staying proactive and informed is key to protecting your systems from RATs.
\ Featured image by freepik
\
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.