and the distribution of digital products.
DM Television
How a $200k Exploit Unfolded at UniLend
 UniLend Finance was exploited for ~$200k
UniLend Finance was exploited for ~$200kOn January 12, 2025, UniLend Finance was exploited for ~$200k due to a flaw in the redeemUnderlying function’s health factor validation. The attacker leveraged flashloans to manipulate collateral calculations, exploiting outdated pool balances and inflated lending shares.
Here’s the Quick Scoop!The UniLend V2 exploit was enabled by vulnerabilities in the redeemUnderlying function's health factor checks.
The attacker leveraged a flash loan to deposit inflated collateral (60M USDC and 6 stETH) into UniLend, borrowed 60.67 stETH using the manipulated health factor, and exploited the flawed balance calculations in userBalanceOftoken.
By bypassing proper checks and inflating collateral values, the attacker repaid the flash loan and withdrew 60.67 stETH (~$200k).
About UniLend FinanceUniLend Protocol is a permissionless decentralized money market protocol with lending and borrowing service through smart contracts. UniLend enables users to utilize their cryptocurrencies by supplying collateral to the network that may be borrowed by pledging over-collateralized cryptocurrencies
Exploit DetailsAttack Transaction: 0x44037
Attacker Address: 0x55F5
Attacker Contract Address: 0x3F81
Vulnerable Contract: 0x7f2E2
At first, the attacker gave max approval of USDC token to Morpho Blue and UnilendV2core. In the same way, wstETH token to Morpho Blue and stETH token to UnlinedV2core, wstETH token.
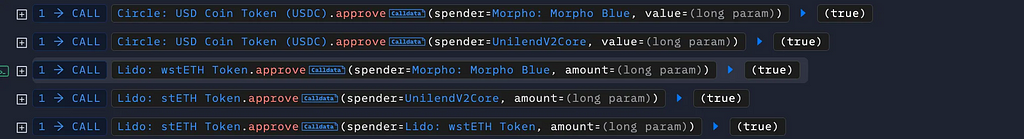
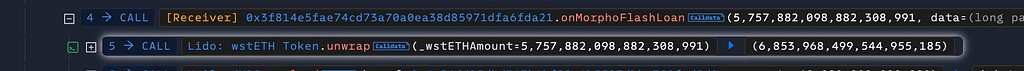
After that, the attacker took a flash loan of 60M USDC and 5 wstETH from Morpho. Then he exchanged borrowed wsETH to stETH and got 6 stETH.
The attacker called lend() twice on UnilendV2Core to deposit 60M USDC and 6 stETH by using flash loan funds.
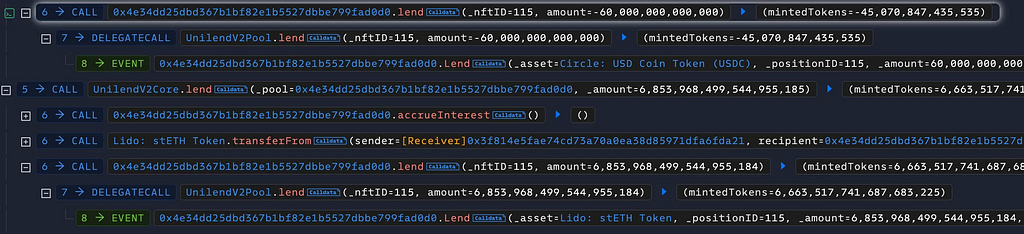
Then he called borrow() by passing recipient as his contract address and borrowed 60.67 stETH since he deposited enough collateral.
The redeemUnderlying() burns the LP position and check the health factor of corresponding _nftID and transfer the token amount to the user.
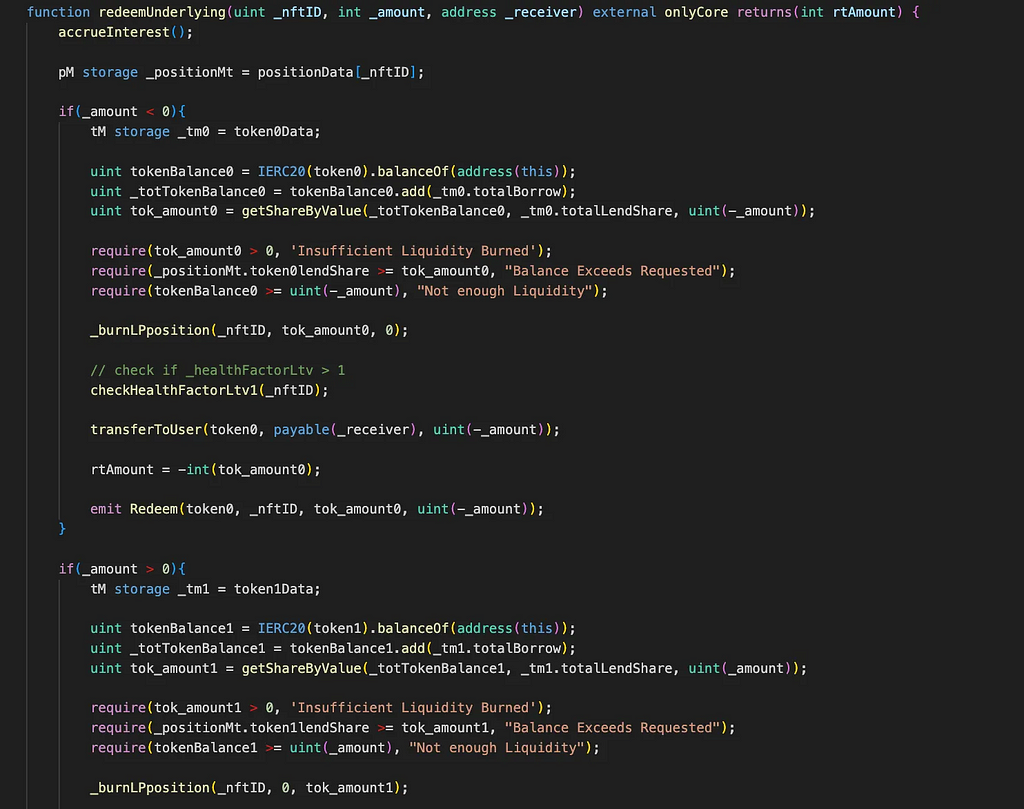
The vulnerability rises in the checkHealthFactorLtv0 and checkHealthFactorLtv1 since these functions totally depends on the userBalanceOftoken0 and userBalanceOftoken1 to check the healthFactor.
In the userBalanceOftoken0, the _lendBalance0 is inflated due to incorrect calculation of user token balance. Since the tokens are not transferred while calculating, it returns inflated shares.
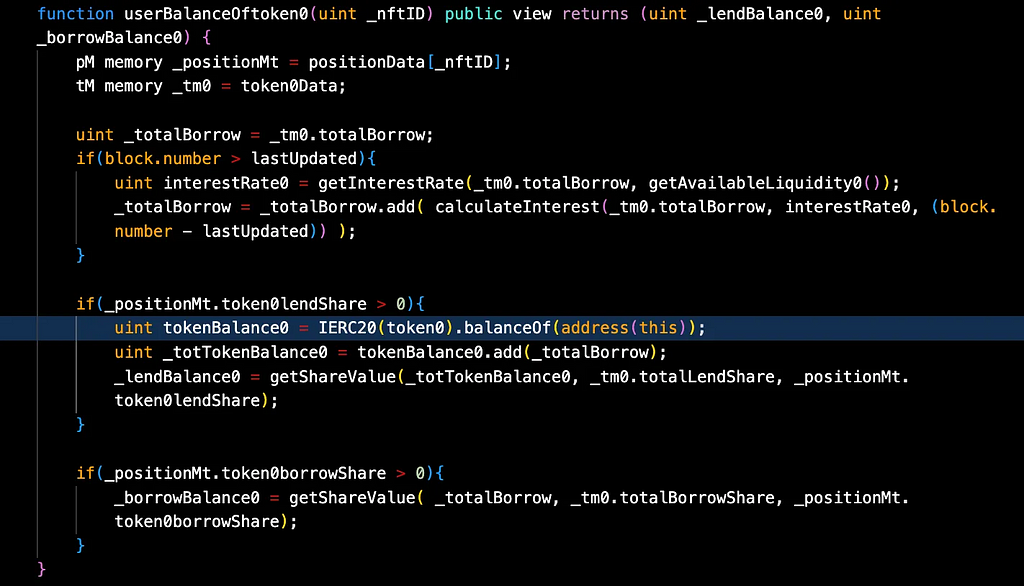
He repaid the flash loan funds by calling redeemUnderlying() twice. After that he transferred 60.67 stETH ( ~$ 200k) to his address 0x55f5 .
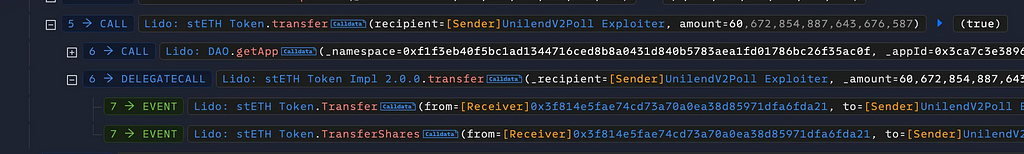 Where Are the Roots of This Problem?
Where Are the Roots of This Problem?The root cause of the UniLend V2 hack lies in the flawed logic of the checkHealthFactorLtv0 and checkHealthFactorLtv1 functions, which depend on userBalanceOftoken0 and userBalanceOftoken1 for health factor validation. These calculations inflated the attacker’s collateral value due to incorrect handling of token balances in _lendBalance0 and _lendBalance1. Specifically, the contract used outdated pool balances that did not account for tokens already allocated or pending transfer, allowing the attacker to bypass health factor checks and withdraw more than permissible collateral.
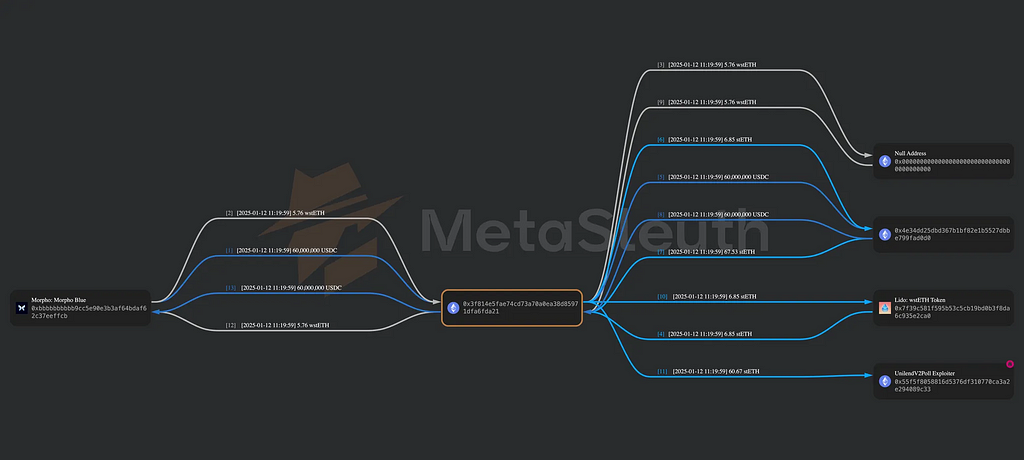
Where Did the Money Go?Want to trace the stolen funds? Here is the flow:
 What Did UniLend Do About It?
What Did UniLend Do About It?The UniLend team has acknowledged the exploit and offered a 20% bounty to the attacker for the safe return of funds.
How Do We Stop This From Happening Again?- Ensure that token balances are updated (e.g., via token transfers) before performing health factor checks. This prevents the use of outdated or inflated balance data in calculations.
- Adjust the sequence in functions like redeemUnderlying to update pool states (e.g., burning LP tokens or transferring collateral) before checking the health factor.
- Collaborate with reputable audit firms like QuillAudits to analyse smart contracts and identify these type of vulnerabilities.
Choosing a reputable Web3 audit firm like QuillAudits ensures that your protocol undergoes rigorous scrutiny from experienced security professionals. QuillAudits specializes in uncovering critical vulnerabilities and providing actionable remediation strategies. Our expertise helps safeguard your project from attacks, ensuring that security issues are addressed proactively.
How a $200k Exploit Unfolded at UniLend was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.