and the distribution of digital products.
DM Television
Facing 2025 Cybersecurity Head-On: Why Ignoring Tech Optimization Could Cost You More Than Data
\ As we approach 2025, the cybersecurity landscape is more treacherous than ever. Businesses are grappling with increasingly sophisticated threats that can cripple operations and tarnish reputations. Cybercriminals are leveraging advanced technologies to exploit vulnerabilities, and organizations that neglect tech optimization are not just risking data loss. They're jeopardizing their entire future.
\ Here at Erbis, we thought it would be great to mark the ==Cybersecurity Awareness Month== by sharing some insights with you. We’ve got some hands-on expertise in protecting sensitive legal and operational data against breaches and ensuring compliance with industry standards. So, let’s get started!
\
The Cybersecurity Landscape in 2024The rise of cybercrime is staggering. According to Statista, global ==cybersecurity breaches are expected to grow by 15% annually, leading to an estimated $15.6 trillion in losses by 2029==. This surge is not merely a statistic; it reflects the reality many businesses face as they navigate a digital world fraught with risk. Ransomware attacks, AI-driven threats, and supply chain vulnerabilities are just a few of the challenges that can devastate companies unprepared for the onslaught.
\ As more organizations adopt remote and hybrid work models, the attack surface expands. Cybercriminals are exploiting unsecured personal devices and networks, making it imperative for businesses to rethink their cybersecurity strategies.
The high cost of inactionThe sad fact is that organizations failing to prioritize tech optimization face numerous challenges:
\
- Financial Losses. As it was projected by industry analytics, the average cost of a data breach has exceeded $4 million in 2024, including ransom payments and lost business.
\
- Regulatory Penalties. With stricter regulations on data protection, non-compliance can lead to hefty fines.
\
- Operational Disruption. Cyberattacks can halt operations, resulting in downtime that affects service delivery and customer satisfaction.
Oftentimes, relying on your in-house IT department might not be enough to combat cyber threats. Maintaining an in-house cybersecurity team equipped to handle these challenges can be prohibitively expensive. ==Skilled professionals demand high salaries due to their expertise, creating a significant financial burden for mid-sized businesses and startups.== Moreover, the ongoing skills gap in the cybersecurity field makes it difficult for organizations to find qualified personnel.
Use case: Custom software solutionsLet’s see what ideas may come to mind.
\ Rather than trying to build an extensive in-house team, businesses should better consider partnering with specialized custom software solutions companies. Usually, these companies have an edge over own IT departments offering such competitive benefits as:
\
Expertise.
With a team of certified engineers experienced in the latest cybersecurity technologies, they can provide tailored solutions that meet specific business needs.
\
Cost Efficiency.
Outsourcing cybersecurity allows organizations to access high-level expertise without the overhead costs associated with maintaining an in-house team.
\
Scalability.
As businesses grow, their cybersecurity needs evolve. Custom software solutions can be adjusted and scaled to meet changing demands without requiring significant additional investment.
\
Focus on Core Business.
By relying on external experts for cybersecurity, organizations can concentrate on their core competencies and strategic initiatives rather than getting bogged down by tech challenges.
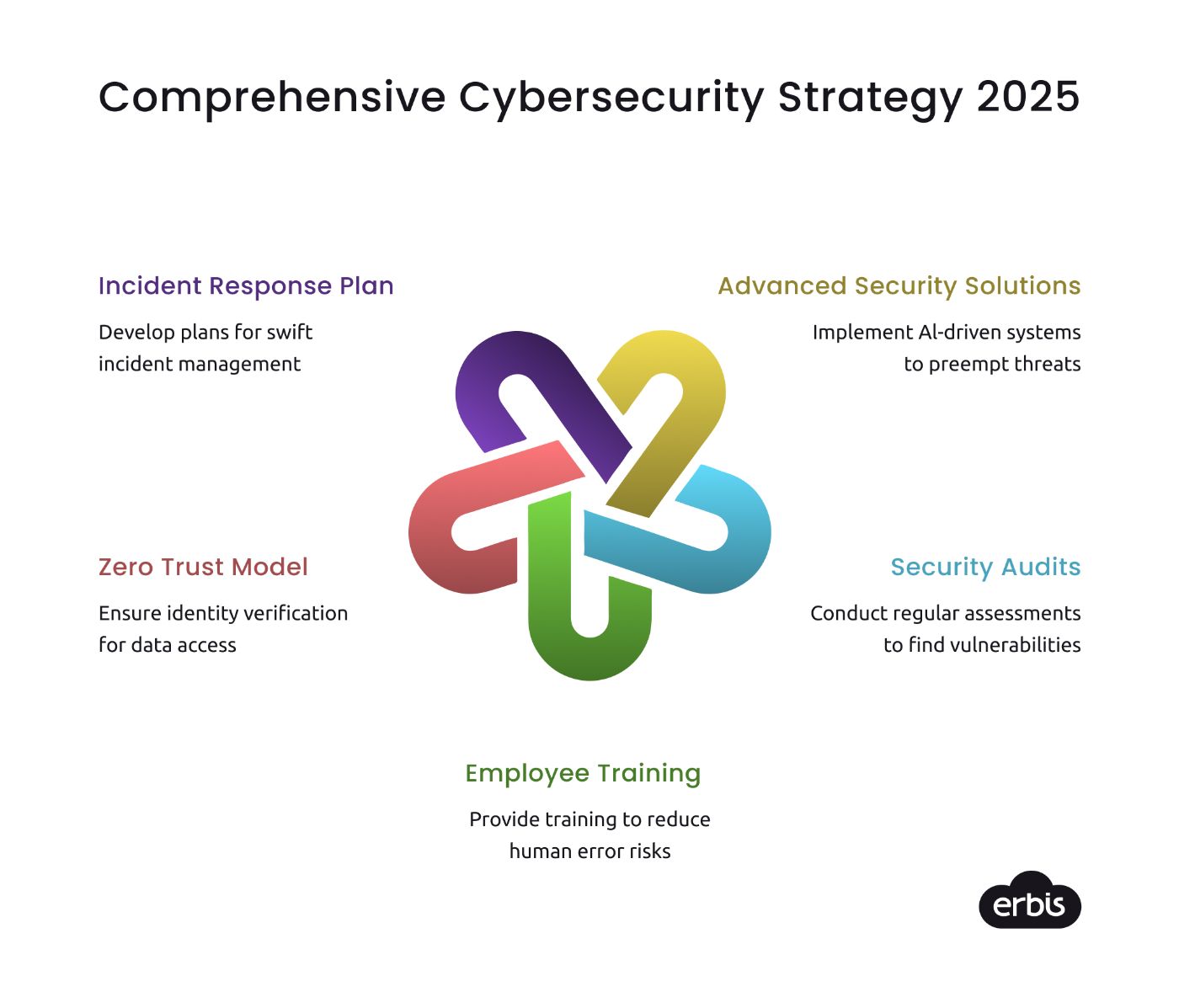
What’s in there for businesses in 2025? IT security costs were predicted to grow by an average of 5.7% annually in 2024. Enhancing the cyber resilience of cybersecurity teams was really the top spending priority for businesses globally in 2023. A recent IBM report reveals that ==adopting security AI and automation can cut breach costs==. Given this, to effectively combat the growing threat landscape, businesses must adopt proactive strategies:
\
Invest in Advanced Security Solutions.
Implement technologies such as AI-driven threat detection systems that can identify and neutralize threats before they escalate.
\
Conduct Regular Security Audits.
Frequent assessments will help identify vulnerabilities within existing systems and processes.
\
Enhance Employee Training.
Regular training sessions on cybersecurity best practices can significantly reduce the risk of human error—one of the leading causes of data breaches.
\
Adopt a Zero Trust Model.
This security framework ensures that trust is never assumed; every user must verify their identity before accessing sensitive data.
\
Develop an Incident Response Plan.
A well-defined plan will enable organizations to respond swiftly to cyber incidents, minimizing damage and recovery time.
\ Here’s a picture related to the list, for those of you who are visual learners like me.
\
Envisioning Cybersecurity in 2025So, what about the future prospects of cybersecurity?
\ Looking ahead to 2025, businesses must be prepared for emerging trends that will shape the cybersecurity landscape:
\
AI-Powered Cyber Attacks.
As AI technology evolves, so do the tactics employed by cybercriminals. Expect more sophisticated attacks that leverage AI for automated threat analysis and vulnerability identification. Organizations must invest in AI-driven defenses to counter these emerging risks effectively.
\
Zero Trust Architecture (ZTA).
ZTA will become essential as remote work continues to rise. This model requires continuous verification of every user and device attempting to access company resources, significantly reducing potential attack vectors.
\
Supply Chain Resilience.
With supply chain attacks on the rise, organizations will need robust measures such as thorough partner screening and regular security audits to protect against cascading effects from interconnected networks.
\
Biometric Authentication.
As security measures evolve, biometric authentication methods like fingerprint scanning will enhance access control but also raise privacy concerns that need careful management.
\
Cloud Security Innovations.
With an anticipated 85% of companies adopting a cloud-first approach by 2025, securing cloud environments will become critical. Businesses must implement cloud-native security measures tailored specifically for multi-cloud strategies.
\
Deepfake Detection Technologies.
As deepfake technology becomes more prevalent, organizations will need advanced tools to detect manipulated content that could lead to misinformation or identity theft.
\
Cyber Insurance Standardization.
As cyber risks evolve, so too will cyber insurance policies, leading to more standardized coverage across providers—making it essential for businesses to stay informed about their options.
As we move deeper into 2024 and beyond, the importance of tech adoption in addressing cybersecurity challenges cannot be overstated. ==Organizations that fail to adapt, risk not only financial losses but also long-term reputational damage==. By leveraging specialized custom software solutions from experts like Erbis, businesses can effectively navigate this complex landscape while focusing on growth and innovation.
\ Ignoring these challenges is no longer an option. Proactive investment in technology is a key to safeguard your business’ future. And maximizing profits along the way. The time to act is now. Your business's resilience depends on it! \n
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.