and the distribution of digital products.
DM Television
Educational Byte: What is a Sidechain and How Does It Work?
\ Blockchains and other Distributed Ledger Technology (DLT) structures aren’t connected, which may hinder some functionality for final users. It’s impossible to just use a certain chain's features and tokens in another, not without an additional system in the middle or very big and risky changes. That’s why sidechains were created.
\ Sidechains are separate chains connected to a main one (like Bitcoin or Obyte) that let their users “transfer” assets and data back and forth. Think of a sidechain as a connected but mostly independent track running alongside the main chain, which lets it experiment with different features—like faster transactions or lower fees—without affecting the main chain’s performance or rules. This way, sidechains can add new capabilities and improve scaling without changing the main chain itself.
\ On the other hand, there are no actual “transfers” happening. Instead, assets on the main chain are locked up in a smart contract or special address, making them temporarily unavailable. In response, an equivalent amount of assets is unlocked or created on the sidechain, where they become available for users. The reverse happens when moving assets back: they’re destroyed on the sidechain, and the original assets are unlocked on the main chain. This locking and unlocking system (called two-way peg) keeps the overall supply constant while allowing assets to be used in both chains.
How Sidechains WorkSidechains are unique because they can use a completely different consensus mechanism from the main chain they’re connected to. While a main chain like Bitcoin might use a slower Proof of Work (PoW), a sidechain could choose a faster method, like Proof of Stake (PoS). On the other hand, given that a sidechain is still dependent upon a main chain, its level of decentralization can vary. A structure offered by a Directed Acyclic Graph (DAG) like Obyte could provide further decentralization of the main chain, and therefore, the sidechain, for instance. Meanwhile, the sidechain would keep enough flexibility to be tailored for specific purposes, like handling high transaction volumes for gaming or DeFi applications, without altering the main chain’s rules or security model.
\
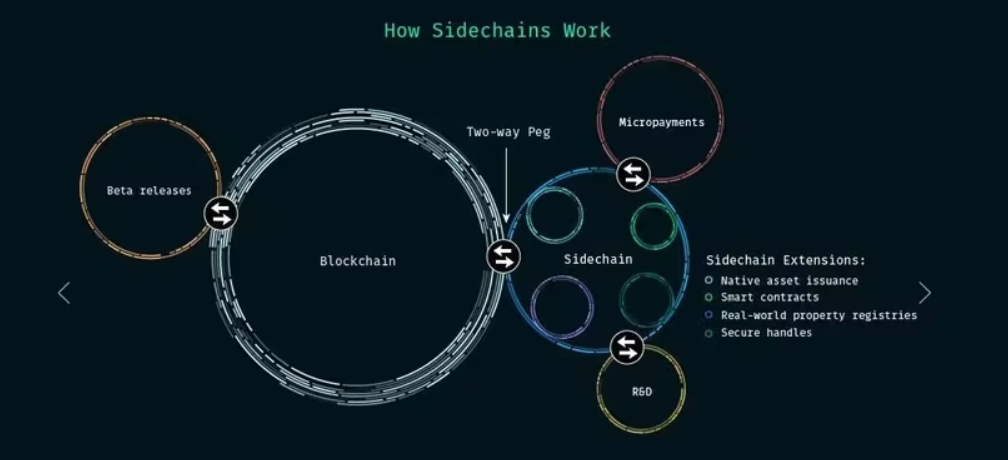
\ Sidechains thus offer a powerful balance: they stay connected to a trusted main chain while giving developers the freedom to create specialized environments for different use cases. Importantly, any security issue or failure that occurs on a sidechain is contained within that sidechain and won’t directly affect the main chain’s security or assets.
\
Potential Use CasesSidechains open up a range of possibilities in the crypto world, especially when it comes to scaling and expanding DLT use cases. One major use is in high-transaction applications like decentralized finance (DeFi) and gaming, where speed and low transaction fees are crucial. Main chains often struggle with congestion and high fees, especially during peak usage times, which can limit their usability. By offloading transactions onto a connected sidechain, users can access faster, more affordable interactions, enhancing the experience for applications that require frequent or high-volume transactions.
\
Another promising use of sidechains is cross-industry collaboration. Different industries, from healthcare to supply chain management, need specific chain setups to address their own unique regulatory and operational needs. Sidechains make it possible to build customized systems that remain connected to a larger network but can be tailored to these specific requirements. For example, a healthcare-oriented sidechain can ensure data privacy and compliance with regulations while still integrating with a broader mainnet for secure, decentralized storage.
\ Finally, privacy-focused applications are increasingly using sidechains to keep sensitive information secure without sacrificing the advantages of decentralized technology. Transactions can be processed on the sidechain with enhanced privacy protocols, and only essential, non-sensitive data can be synced with the main chain. This makes sidechains valuable for applications like financial trading and private contracts, where confidentiality is paramount but transparency is still necessary.
\ Obyte’s latest infrastructure updates pave the way for sidechains by adding features that make integration smoother and more efficient. Sidechains can now leverage Obyte’s DAG-based system to organize their data without needing their own consensus mechanism. This makes scaling easier, especially for applications needing fast, reliable data handling. With all these new benefits, Obyte empowers developers to build versatile, scalable sidechains.
\
:::info Featured Vector Image by fullvector / Freepik
:::
\n
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.
