and the distribution of digital products.
DM Television
CESS Network: A Deep Dive into Programmable Data Value Infrastructure
- CESS offers a decentralized approach to data value infrastructure, prioritizing security and user control to address the limitations of centralized infrastructure systems.
- CESS leverages a distributed network, advanced encryption, and a Proof mechanism with a built-in blockchain-based disaster recovery system to enhance data integrity, resilience, and privacy. By engaging with regulators and policymakers, CESS ensures compliance while maintaining a decentralized framework for frequently accessed "hot" storage.
- CESS's architecture is designed to integrate with the DePIN, AI, and DeSci ecosystems, fostering innovation and collaboration across such sectors.
- CESS is building a sustainable ecosystem through 14 testnet iterations, community engagement, and regulatory partnerships. Its focus on data sovereignty, security, and compliance highlights its potential to reshape data value distribution in the decentralized web.
In the rapidly evolving Web3 landscape, the need for secure, decentralized data infrastructure has become crucial. Traditional centralized infrastructures often face vulnerabilities related to data privacy, security breaches, and single points of failure. CESS offers a blockchain-based alternative, addressing these issues and providing a foundational platform for decentralized data management, enabling the exchange and circulation of data value securely and efficiently. By prioritizing data sovereignty and user control, CESS allows for data monetization in the digital era, empowering users with the right to earn from their digital assets. CESS is more than just a storage solution; it's a foundational infrastructure designed to support the growth of decentralized applications across various sectors, including DePIN, AI, and DeSci. The platform's architecture integrates a distributed storage network, Layer-1 blockchain, and a high-speed content delivery network to ensure data integrity, privacy, and accessibility.
Website / X (Twitter) / Discord / Telegram
CESS: Decentralized Data Value InfrastructureCurrently, the data value industry faces significant challenges, including data privacy breaches, data silos, and centralized control over data. As data volumes grow exponentially, traditional centralized infrastructures are no longer sufficient to meet the increasingly complex demands. Data security, compliance, and empowering users with control over their data have become pressing issues. In the age of AI, these problems are further amplified, as AI systems rely heavily on data transparency, provenance, and authentication to build user trust. In line with this ethos, CESS is building a decentralized data value infrastructure to address these industry pain points through blockchain technology. In addition to providing storage or content delivery network resources, CESS aims to give users full control over their data through decentralized management.
With CESS, users can transform their data into valuable assets, realizing data monetization. CESS ensures data security and privacy while enabling the flow and exchange of data value across different applications, unlocking data as an asset. By unlocking this value, CESS promotes an equitable and open digital economy for various industries, ultimately enabling many users to benefit from their own data. CESS presents sovereign, scalable, secure, and privacy-preserving data infrastructure, enabling seamless data sharing and collaboration across industries. Existing centralized data infrastructure providers and decentralized storage solutions each have inherent limitations, including data loss, slow retrieval speeds, and unclear data sovereignty. CESS seeks to address these shortcomings by offering a decentralized data infrastructure that prioritizes transparency, efficiency, and equitable participation within its ecosystem.
To achieve this, CESS implements several key innovations:
- Random Rotational Selection (R²S): A proprietary consensus mechanism that selects 11 new on-duty consensus nodes per era through a verifiable randomized process, ensuring fairness and decentralization. This mechanism also integrates a credit score system that resets each era, ensuring all eligible participants have an equal opportunity to become consensus nodes.
- Proof of Idle Space (PoIS) and Proof of Data Reduplication and Recovery (PoDR²): PoIS ensures storage miners provide idle space as they claim, while PoDR² allows for data security, integrity, and availability.
- Proxy Re-encryption Technology (PReT): Restricts data visibility to authorized users only, reinforcing privacy and security while preventing unauthorized access.
- CESS AI Agent Hub: Provides a decentralized entry point for AI agents, fostering collaboration across AI-driven applications.
- CESS AI-LINK: Enables collaborative AI model training in a decentralized setting. Participants may contribute without exposing their original data, ensuring confidentiality and data sovereignty.
- Multi-format Data Right Confirmation (MDRC): Assigns a unique data certificate ID to each file for data rights protection by extracting a data fingerprint. The MDRC can detect connections between data sets by comparing these digital fingerprints. This connection serves as evidence of the data's origin, enhancing copyright protection.
By integrating these mechanisms, CESS aims to establish a high-performance decentralized storage ecosystem well-suited for AI applications, decentralized GPU networks, and secure data sharing for researchers, positioning itself as a key enabler of innovation in the DePIN, AI, and DeSci ecosystems.
ArchitectureCESS utilizes a layered and loosely coupled system architecture, divided into the CESS Protocol Suite and XESS AI Protocol Suite. The CESS Protocol Suite consists of a blockchain service layer, distributed storage resources, and a decentralized content delivery layer, while the XESS AI Protocol Suite integrates AI technologies to support secure and privacy-preserving collaborative model training on the CESS network.
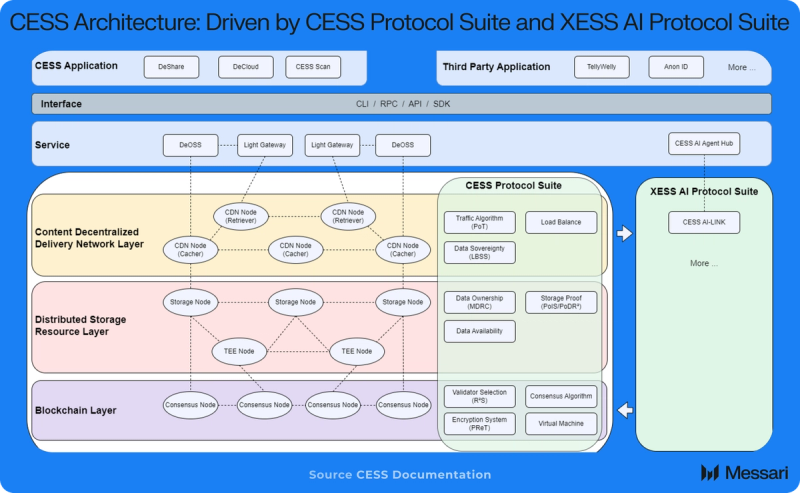
The CESS network architecture combines decentralized cloud storage with a Content Decentralized Delivery Network (CD²N) to offer flexible and scalable solutions for decentralized data storage and real-time sharing. The Content Decentralized Delivery Network optimizes data delivery and retrieval, ensuring that data can be accessed quickly and efficiently, regardless of the user's location. This is achieved through a network of geographically distributed nodes that cache and serve content. CESS also ensures data security and integrity using proprietary technologies, including data ownership protection, Proof of Data Reduplication and Recovery (PoDR²), Multi-format Data Rights Confirmation (MDRC), and Proxy Re-encryption Technology (PReT).
The CESS Protocol Suite includes three layers:
- The Blockchain Layer: Provides blockchain services for the entire CESS network, including encouraging unused storage resources and computational resources to join the CESS network to provide data storage, data rights confirmation, and other services for the application layer.
- The Distributed Storage Resource Layer: Uses virtualization technology to capture the integration and pooling of storage resources. The infrastructure consists of Storage Nodes and TEE Nodes.
- The Content Decentralized Delivery Network Layer (CD²N): Utilizes content caching technology to ensure rapid distribution of stored data, involving both data Cacher Nodes and Retriever Nodes.
Building on this layered architecture, CESS further enhances its network capabilities through the XESS AI Protocol Suite, which integrates AI-driven solutions for secure and decentralized data processing. At the core of the XESS AI Protocol Suite is CESS AI-LINK, designed to enhance data privacy in AI training. AI-LINK enables AI models to be trained in a decentralized network without exposing original data, ensuring confidentiality and integrity while allowing organizations to benefit from more secure and efficient AI development.
The Interface acts as a bridge, facilitating interaction and communication between the CESS Protocol Suite and the XESS AI Protocol Suite. It establishes a standardized set of rules and conventions, ensuring seamless coordination among components and supporting CESS's overall functionality. Additionally, it enables the creation, management, and execution of processes across the network.
CESS has undergone extensive testing through 14 iterations of its testnet, codenamed "Venus," culminating in Venus v0.7.7, further demonstrating CESS's commitment to a robust and reliable infrastructure. CESS’s testnet evolution has been marked by critical advancements in economic incentives, security, scalability, and regulatory compliance. The platform transitioned to integrate R²S consensus and refined staking, penalties, and reward mechanisms to incentivize network participation. Security was enhanced through SGX-based TEE Workers, hardware-backed storage proofs (PoDR², PoIS), and encrypted cross-platform SDKs for data privacy. Scalability and efficiency improved with direct P2P data transmission (CD²N with advancing caching and indexing technologies for high-frequency data access) and optimized file storage processes - reducing verification overhead and enhancing retrieval speeds. Regulatory alignment was strengthened with Location-Based Storage Selection (LBSS), which allows users to decide the region where data is stored, ensuring users store data within jurisdictional boundaries. The network’s cross-chain capabilities, EVM integration, and developer-friendly SDKs further establish CESS as a leading decentralized storage solution for DePIN, AI, and DeSci ecosystems. These testnets have demonstrated the network's ability to scale, reaching 22 consensus nodes, 8,055 storage nodes, 44.73 PiB of verified storage space, and 56.33 PiB of total storage space. This extensive testing and scaling demonstrate CESS's readiness to handle real-world data storage demands.
Security InfrastructureCESS prioritizes security and privacy by leveraging robust encryption to protect user information from unauthorized access and tampering. To further reinforce data sovereignty, CESS has implemented an onchain Multiformat Data Rights Confirmation Mechanism (MDRC), which assigns a unique data certificate ID to each file by extracting its data fingerprint. This ID comparison system enables the detection and prevention of data rights violations, safeguarding premium content quality. For instance, if a content creator uploads an original piece of music to the CESS network, MDRC will generate a unique digital fingerprint for that file. If another user later uploads a similar piece of music, MDRC will evaluate the resemblance between the two digital fingerprints to identify any potential copyright infringement. MDRC can identify relationships between different data sets by analyzing these digital fingerprints, providing verifiable proof of origin. Additionally, CESS has implemented the Proof of Data Reduplication and Recovery (PoDR²) mechanism, which reassures data availability using Erasure Coding (EC) and features a blockchain-based disaster recovery system. PoDR² breaks data into fragments, allowing it to be expanded, encoded with redundant data pieces, and stored across different storage miners. Lastly, the Location-Based Storage Selection (LBSS) feature allows users to choose specific geographic regions for data storage, addressing compliance requirements with international and regional data protection laws like GDPR, HIPAA, and CCPA. This functionality is crucial for industries dealing with sensitive data and operating in multiple jurisdictions, highlighting CESS's focus on enterprise-grade solutions. For example, a healthcare provider might need to store patient data within a specific country to comply with HIPAA regulations.
AI and Decentralized Infrastructure IntegrationAI training requires frequent data operations and substantial storage capacity. The CESS network meets these demands with scalable, cost-efficient storage and effective data management.
To enhance trust in AI systems, the usage and behavior of the AI model, along with its training data and sources, need to be trustworthy and verifiable. The transparent and immutable blockchain provides traceable data sources, ensuring the integrity of the AI model and its usage or performance, thus empowering responsible AI. This foundation supports the development of responsible AI. A core aspect of CESS's architecture is its integration with the DePIN, AI, and DeSci ecosystems. Decentralized Physical Infrastructure Networks (DePINs) incentivize the distribution of network nodes globally, ensuring the decentralized nature of the storage system. DePINs provide the physical infrastructure needed to support decentralized applications, and CESS leverages this infrastructure to create a robust and resilient storage network. CESS's support for AI innovations is exemplified by its AI Agent Hub, launched in January 2025. This hub is a decentralized platform for aggregating and deploying AI agents across various industries. Furthermore, it provides a marketplace for AI agents, allowing developers to create and deploy AI models that can be used across various industries. Additionally, CESS integrates AI-LINK, a Byzantine-Robust system designed to enhance data privacy in AI training. AI-LINK enables AI models to be trained in a decentralized network without exposing original data, ensuring confidentiality and integrity while allowing organizations to benefit from more secure and efficient AI development.
Decentralized Science (DeSci) and Data SovereigntyCESS’s integration with Decentralized Science (DeSci) empowers researchers with secure, decentralized platforms for data sharing and collaboration, which is particularly crucial for handling sensitive research data while adhering to privacy regulations and promoting open access to scientific knowledge. Creators of sensitive data may create a paywall for their stored data, allowing the data creator to earn or benefit from their knowledge. CESS's strategy to reshape data value distribution is rooted in its commitment to secure, privacy-focused, and sovereign data storage. By empowering users with control over their data, CESS directly addresses the concerns surrounding centralized data systems where users often lack transparency and control.
Ecosystem Development and ToolsCESS has developed a suite of tools to enhance the usability and functionality of its ecosystem. These include:
- Decentralized Object Storage Service (DeOSS) is a decentralized Simple Storage Service (Amazon S3) that serves as a gateway to the CESS network.
- DeShare is a decentralized file-sharing and exchange tool that enables secure, fast, and permissioned data sharing with full user control.
- DeCloud is a decentralized cloud storage platform with a file categorization system and layered permission management.
- CESS Scan as a blockchain explorer.
- CESS Light Wallet for managing digital assets.
These tools reflect CESS's focus on providing a comprehensive and user-friendly platform for decentralized storage. DeOSS provides a scalable and efficient solution for storing and retrieving data, while DeShare enables secure and private file sharing. The CESS Scan blockchain explorer allows users to track transactions and monitor network activity, and the CESS Light Wallet provides a secure and convenient way to manage digital assets. The development of these tools has been documented in monthly technical reports, demonstrating a commitment to transparency and community engagement.
The ongoing development and testing through Venus testnet and active community engagement initiatives, like the CESS Course and the Global Ambassador Program, reinforce CESS's long-term vision of building a sustainable ecosystem. The CESS Course provides educational resources for developers and users, while the Global Ambassador Program fosters community participation and promotes the platform’s adoption.
CESS's pledge to secure “hot” storage in a decentralized system is central to its value proposition. By addressing the specific vulnerabilities associated with frequently accessed data in a distributed environment, CESS offers a unique solution within the decentralized storage landscape.
With a strong focus on security, scalability, and ecosystem integrations, alongside active community engagement and participation in industry events and policy discussions, CESS is positioned as a key player in the evolution of decentralized cloud storage. The platform's ability to provide secure and reliable storage for frequently accessed data makes it an attractive solution for businesses and individuals who need to store and retrieve data quickly and efficiently.
Industry EngagementFollowing the 2024 U.S. Presidential Election, CESS officially joined the Government Blockchain Association (GBA), reinforcing its commitment to advancing decentralized technology adoption in government, finance, and public infrastructure. As a new GBA member, CESS will actively collaborate on blockchain initiatives, furthering its mission to enhance data sovereignty, security, and enterprise adoption. This aligns with their ongoing regulatory engagement, including participation in the DePIN Briefing on Capitol Hill and contributions to industry standards for decentralized storage protocols through IEEE.
CESS's involvement with the Blockchain Association and the GBA, particularly its participation in policy discussions related to DePIN and national security, further highlights its dedication to shaping the regulatory landscape for decentralized technologies. This proactive approach to policy engagement demonstrates their willingness to work with regulators to create a clear and consistent regulatory framework for decentralized technologies.
CESS has also secured approval from the IEEE Computer Society/Blockchain and Distributed Ledgers (C/BDL) Standards Committee for the IEEE P3220.02 Standard for Blockchain-Based Decentralized Storage Protocol Specification, marking a major milestone in the standardization and global adoption of decentralized storage technology. This achievement reinforces CESS’s technical leadership in blockchain-based data infrastructure and aligns with its above-mentioned mission. By addressing industry challenges such as low storage utilization and slow retrieval speeds, CESS sets a new benchmark for reliability and scalability in Web3 storage. Additionally, CESS will collaborate with IEEE to host seminars and industry discussions aimed at expanding decentralized storage frameworks and fostering innovation.
Closing SummaryCESS presents a compelling vision for the future of decentralized data value infrastructure. By prioritizing security, privacy, and user control, CESS aims to address the limitations of traditional centralized systems and empower individuals and organizations with a more secure and efficient method for managing their data. The platform's architecture, which integrates a distributed storage network, a Layer-1 blockchain, and a high-speed content delivery network, is designed to ensure data integrity, privacy, and accessibility. CESS's integration with the DePIN, AI, and DeSci ecosystems further enhances its value proposition, fostering innovation and collaboration across these sectors. The platform's support for AI agents, decentralized GPU networks, and secure data sharing for researchers positions it as a key infrastructure provider for data value applications through blockchain infrastructure.
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.