and the distribution of digital products.
In the Blink of an LED, Secrets Slip Away: The Rise of Optical Data Theft
For decades, air-gapped systems which are physically isolated from external networks have been the last line of defense for high-security environments: nuclear facilities, defense networks, R&D labs, and critical infrastructure. But in 2025, even isolation isn't enough. Why? Because attackers have learned to blink the data out.
Welcome to the covert world of optical data exfiltration, where malware manipulates LEDs, Morse code becomes a medium, and surveillance cameras act as listening posts.
Leaking Data with LightThe technique is deceptively simple, yet incredibly effective.
A compromised air-gapped system is infected with specialized malware via insider access, compromised USB, or supply chain infiltration.
\
The malware encodes sensitive data (passwords, cryptographic keys, documents) into binary or Morse code.
\
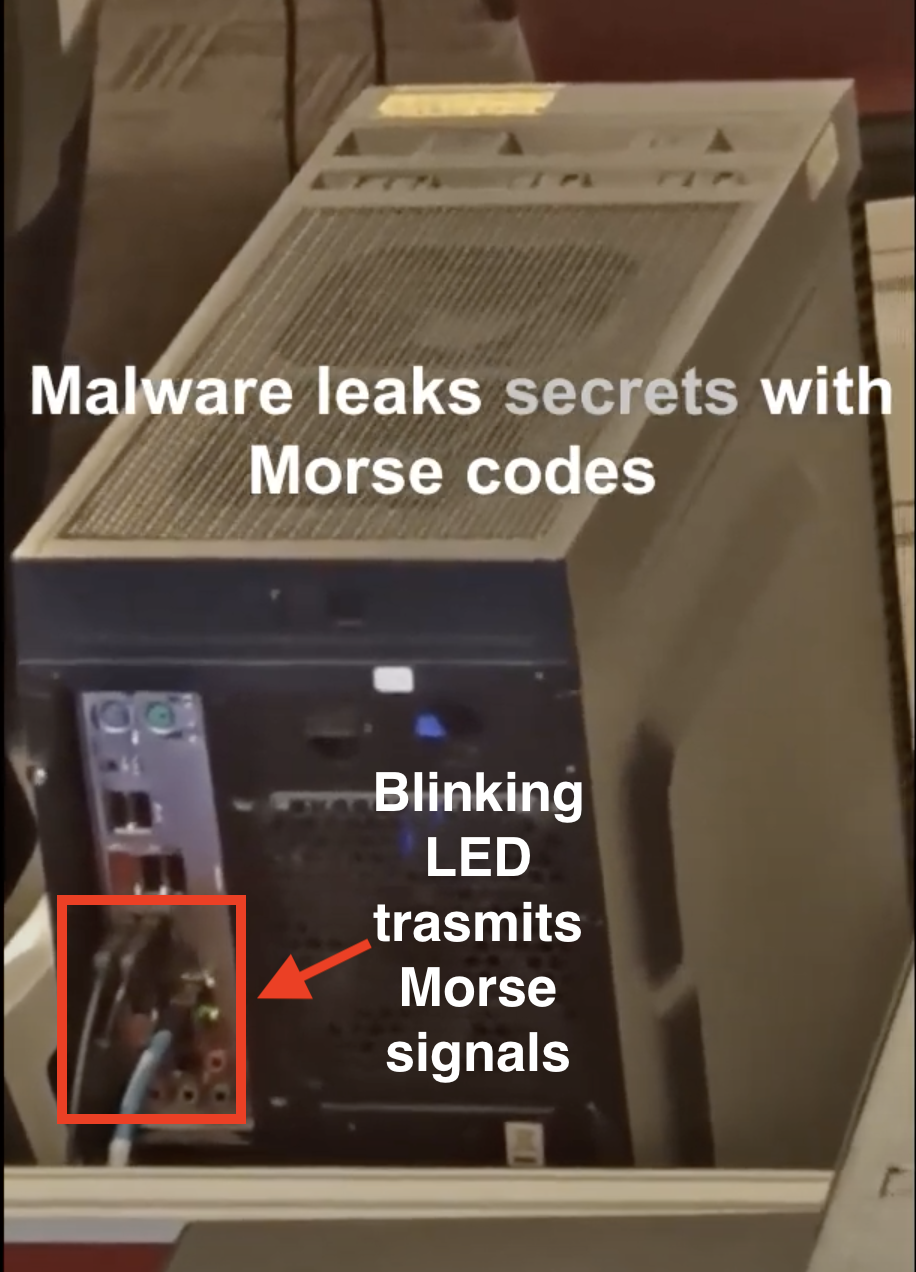
The data is then modulated into optical signals by blinking an on-board LED, typically:
HDD activity LED
Keyboard indicators (Num Lock, Caps Lock
Router port status LEDs
IR LEDs in surveillance cameras
\
An attacker with line-of-sight access using a smartphone, camera drone, telescope, or hijacked CCTV, records the blinking patterns.
\
On the attacker’s side, the optical data is decoded into plaintext using signal processing or computer vision tools.
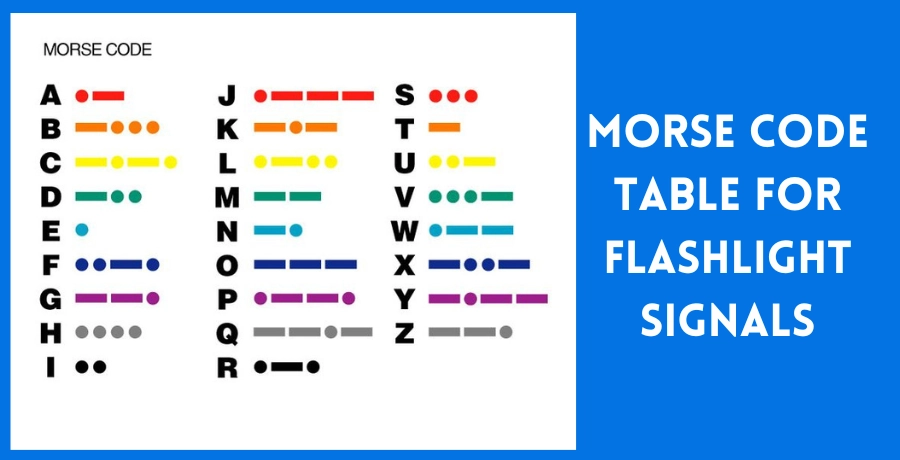
Let’s break it down with an example using a surveillance camera with an IR LED:
Step 1: Malware Deployment- Malware is delivered via infected firmware, insider USB drive, or a pre-installed rootkit.
- The malware gains access to the camera's IR LED controls, often available via low-level APIs or debug interfaces.
Sensitive data (e.g., "RootPassword123") is converted to binary or Morse code:
`"R" in Morse: .-. ` Or `in binary: 01010010`- Data is framed with start/stop sequences to aid synchronization during decoding.
- Timing is critical: On-off intervals must be consistent (e.g., 100 ms on, 100 ms off per bit).
The IR LED blinks rapidly and is invisible to the human eye, but detectable to most cameras or IR sensors.
`LED on = binary 1` `LED off = binary 0`- Transmission rates vary from 10–100 bits per second, depending on LED type and brightness.
Attacker positions a camera within LOS (line-of-sight). Could be:
- A tampered building camera
- Drone-mounted camera at night
- Smartphone from a nearby building
- Frame-by-frame analysis captures the blinking pattern.
- OpenCV or similar libraries are used to extract and decode the signal.
Software demodulates the light pulses, reconstructs the binary stream, and decodes it back into human-readable content.
Real-World ImplementationsThese aren’t just theoretical. Here are some notable proof-of-concept attacks that have demonstrated this technique in the wild:
aIR-Jumper (Ben-Gurion University):
- Attack Medium: IR LEDs on surveillance cameras
- Data Rate: ~20 bits per second
- Range: Up to 25 meters
LED-it-GO
- Attack Medium: Hard drive activity LEDs
- Data Rate: ~100 bits per second
- Range: Up to 30 meters
xLED
- Attack Medium: Keyboard indicator LEDs (Caps Lock, Num Lock, etc.)
- Data Rate: ~60 bits per second
- Range: Up to 20 meters
Glowworm
- Attack Medium: Audio-to-light leakage from power LEDs
- Data Rate: Passive signal leakage, not encoded by malware
- Range: Detectable with line-of-sight sensors
\
This attack is especially dangerous in:
- High-security air-gapped labs
- Industrial control systems (ICS)
- Secure server rooms with exposed LEDs
- Offices using IR-equipped surveillance for night monitoring
If you have:
- Line-of-sight LEDs,
- Malware infection vector,
- Surveillance infrastructure, then, you have a viable covert exfiltration channel.
Mitigation requires a multi-layered approach:
1) Physical Controls
Block LEDs with opaque tape or shield covers.
- Use blackout enclosures or anti-IR glass in sensitive areas.
- Place sensitive systems in non-transparent, enclosed environments.
2). Monitoring
- Detect unauthorized LED blinking patterns using optical sensors or machine learning-based anomaly detection.
- Log and audit LED usage via firmware (where applicable).
3). Firmware & OS Hardening
- Disable or isolate camera LED control APIs unless strictly necessary.
- Deploy BIOS/firmware validation tools in air-gapped systems.
- Disable keyboard LEDs and router port LEDs where unused.
The blink of an LED was once harmless—a passive sign of activity. But in 2025, even a flicker can be a cyber whisper, bleeding secrets into the night. In a world where radio silence is no longer enough, organizations must now think in photons as well as packets.
So, the next time your devices start blinking oddly, don’t call IT, call the CIA.
\
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.