and the distribution of digital products.
13 Cybercrime Facts That Will Give You Chills
\ Cybercriminals love to give new meaning to the phrase “trick or treat.”
\ Through cyber attacks, phishing, ransomware, and data breaches, bad guys love causing mayhem for businesses and consumers. But their actions aren’t chalked up to the pranks one would expect on All Hallows’ Eve. Their impacts are far more costly and devastating to victims.
\ Knowing this, let’s explore 13 cybercrime facts that will make your hair stand on end.
Scary Financial Cybercrime Facts and Stats 1. Ransomware Netted Threat Actors More Than $1.1B in Ill-Gotten GainsWhen bad guys come knocking, I promise they’re not looking for your Butterfingers or Reese’s cups. They’re looking for much bigger payouts than candy — we’re talking hundreds, thousands, or even millions of dollars. A report from Chainalysis shows that the ransomware payments bad guys received in 2023 exceeded $1.1 billion.
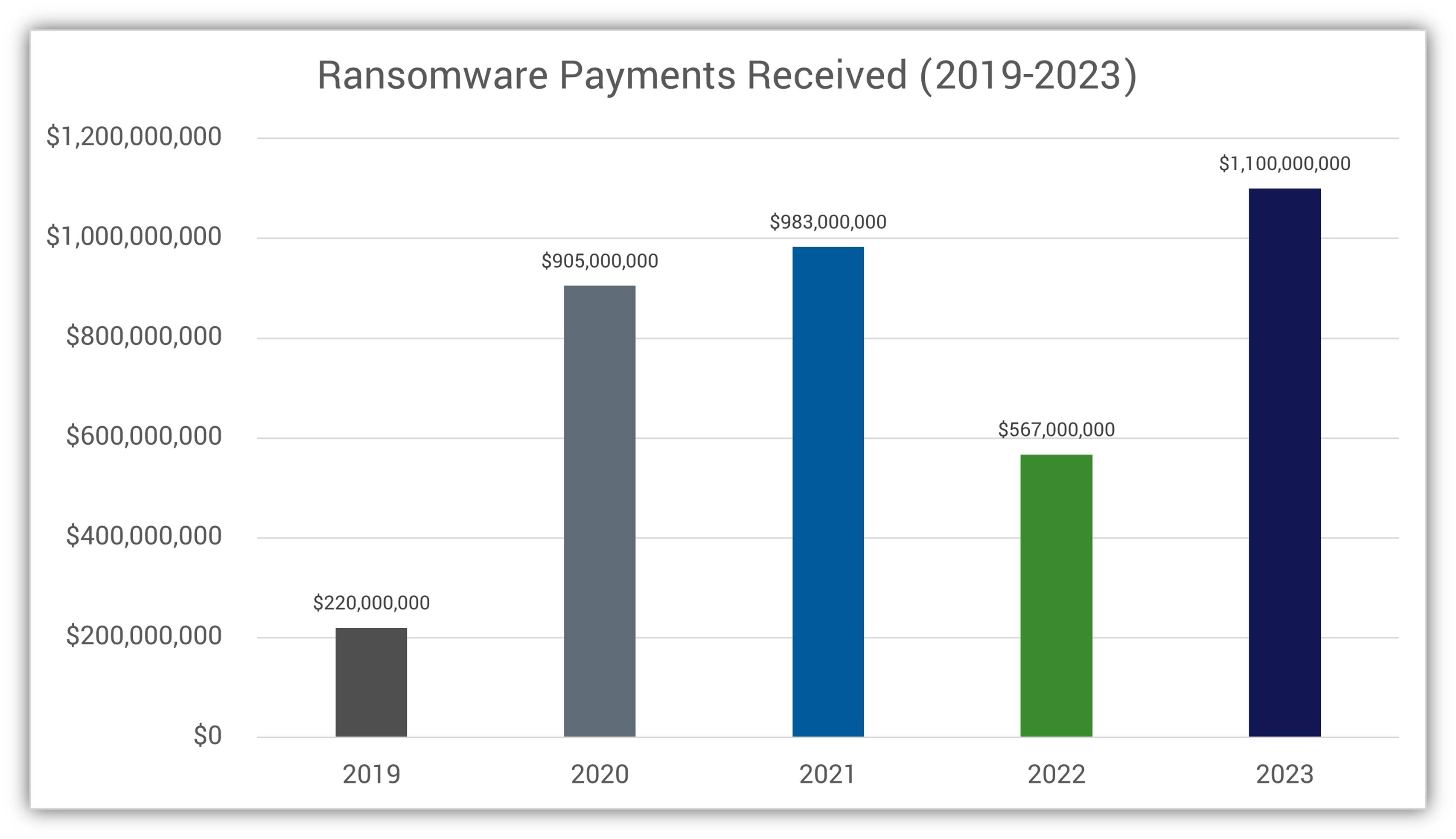
\ For comparison, the total amount they received in ransom payments in 2023 could have bought more than seven F-22 Raptor fighter jets! Keep in mind that each of these machines of war comes with a hefty price tag of $143 million per unit (according to the Air Force’s August 2022 data).
\ Man… that must mean a lot of companies ended up shelling out for ransomware payments. Not necessarily as many as you think, based on our next cybercrime fact…
2. One Company Paid $75 Million as a Ransomware Demand in 2024Simply put, ransomware demands can drain the life right out of a company. According to Zscaler, one company paid this enormous sum to the Dark Angels ransomware group, which has a penchant for targeting critical infrastructure sector companies.
\ For perspective, that single ransom cost the same amount as what Google dedicated to fund its AI Opportunity Fund.
3. 51% of Organizations Lost $5-$25 Million to AI-Related ThreatsRegardless of whether the cause was an AI-based or AI-driven threat, more than half of the organizations surveyed by Biocatch shelled out between $5 and $25 million in 2023. A full 12% of respondents said they faced at least $25 million in damages. We’re not talking pocket change here; that’s the estimated cost of Angelina Jolie’s Hollywood mansion:
https://www.youtube.com/watch?v=oOEVkFk1008&embedable=true
\ Sadly, only 3% indicated that they had no losses from these threats, meaning that 97% suffered losses in one way or another.
4. True Cost of Fraud to Older Adults Thought to Top $61.5 BillionData from the U.S. Federal Trade Commission (FTC) shows that older adults reported losses topping $1.9 billion in 2023. However, again, that number represents only the reported losses. The agency’s report indicates that the true fraud costs to older adults may really top $61 billion. Why? Because many frauds go unreported.
\ The number of older adults who reported falling for scams with losses of $100k increased “more than threefold since 2020.”
Spooky AI-Related Cybercrime Facts 5. AI-Based Cyber Threats Aren’t Going Anywhere and Are Expected to RiseThe FBI warns that [cybercriminals are increasingly using generative AI technologies]() to carry out cyber attacks. In particular, generative AI is being used for various fraud scams.
\ For example, AI-based virtual kidnapping scams are increasing. In this type of scenario, a bad guy uses data scoured from videos and online profiles to synthesize information and even voice samples of individuals to mimic real people. They can use generative AI technology to create deepfake photos, videos, and audio content that looks realistic and make it appear like someone you know or love — a friend, family member, coworker, or another loved one — is in danger.
\ A perfect example of this can be seen in AI-based kidnapping scams. Here’s a video about real-world AI-based phone scams that targeted people in St. Louis County:
\ https://www.youtube.com/watch?v=84gYLF2r2lo&embedable=true
6. >7 in 10 Financial Companies Face Bad Guys Using Synthetic Identities72% of Biocatch’s survey respondents (report previously cited) indicated that in addition to traditional fraud issues, they’re also having bad guys use synthetic identities to carry out financial transactions, apply for loans and credit cards, and open new bank accounts.
\ Not sure what synthetic identities are? They’re basically new identities that are typically created by combining real and fake personally identifiable information (PII).
\ Unfortunately for the good guys, these mashed phony identities typically trick traditional fraud detection tools, meaning they don’t get flagged and may go unnoticed. Biocatch’s research indicates that while organizations are “largely able to uncover these synthetic identities within three months,” we know that a lot of damage can occur within that time.
\ Only 16% indicate they’re able to identify these synth IDs within 24 hours.
\
7. Synthetic IDs Expose Financial Lenders to $3.1 Billion in Potential LossesSynthetic identities are haunting businesses — financial institutions in particular. TransUnion’s 2024 State of Omnichannel Fraud Report data indicates that U.S. lenders for various types of credit cards and loans had a record number of accounts opened at the end of 2023.
\ The 2023 end-of-year estimated exposure of $3.1 billion is up from $2.8 billion for EOY 2022 and $2.1 billion for EOY 2020.
\
8. GenAI Makes Sophisticated Attacks More Accessible and EffectiveAdvanced phishing attacks, particularly when paired with generative AI and sophisticated deepfake technologies, are highly effective methods for cybercriminals. These intelligence tools breathe new life into social engineering attacks, making them more targeted, authentic, and effective.
\ A partner article published by The Hacker News about research from Token and Datos Insights nicely sums up this growing concern:
\
“Phishing and ransomware attacks were once the exclusive realm of expert cybercriminals, but with the advent of generative AI and new cybercrime tools, launching these attacks has become accessible to anyone with access to the dark web, which is anyone with a computing device and an internet connection.”
\ In its 2025 Homeland Threat Assessment, the U.S. Department of Homeland Security’s Office of Intelligence and Analysis underscores the national security implications of these technologies in the coming year:
\
\ “In 2025, we expect malicious cyber actors will continue to use advancements in generative AI to incrementally enhance their ability to develop malware, vulnerability scanning, and exploit tools and to improve their social engineering tactics and operations. Adversarial states will continue to use AI in their malign influence campaigns as the technology lowers technical thresholds and improves adversaries’ abilities to effectively personalize and scale more credible messages for target audiences.”
\
9. Social Engineering/ BEC Attacks Are Up 1,760%, Largely Thanks to AI\ Data from Perception Point’s 2024 Annual Report: Cybersecurity Trends & Insights” report indicates that number of business email compromise (BEC) attacks rose from 1% in 2022 to nearly 19% of all attacks in 2023.
\ The company says that BEC attacks demonstrating impersonation, phishing, and social engineering techniques are “supercharged” by generative AI. Furthermore, the company’s previously sponsored research (performed by Osterman Research) showed that 91.1% of organizations reportedly experienced cyber attacks stemming from GenAI-enhanced emails.
Scary CyberCrime Facts About Advances in Methods & Techniques 10. Data Exfiltration Is Faster Than Ever (Sometimes Taking Less Than a Day!)Cybercriminals don’t have to don a flight suit costume and aviator glasses to feel the need for speed. When it comes to data exfiltration, Palo Alto’s Unit 42 Incident Response team reports that it’s occurring faster than ever before:
\
“In almost 45% of our cases this year, attackers exfiltrated data in less than a day after compromise. That means that almost half the time, organizations must respond within hours to stop them.”
\ This means that in many cases, attackers have either engaged in or completed their exfiltration before an organization has time to assemble its response team and plan.
\
11. 10+ Billion New & Passwords Circulate in a Single Data BreachRemember the RockYou2024 leak? That file, shared by a threat actor who goes by the name ObamaCare, included a whopping 10 billion passwords.
\
- The good news: CyberNews reports that not all of the passwords were new, meaning that some of the passwords on the list were exposed in previous data breaches. Like… these passwords were collected from more than 4,000 databases over 20+ years. So, yes, the list includes current passwords, but it also includes a lot of old ones that, hopefully, are no longer valid.
- The bad news: Users are slow or neglectful when it comes to changing or updating compromised passwords. For example, a study commissioned by Forbes Advisor and conducted by Talker Research indicates that only 68% of users changed their passwords “across multiple accounts after their password was compromised.” Furthermore, only two in five users change passwords when prompted rather than changing them proactively.
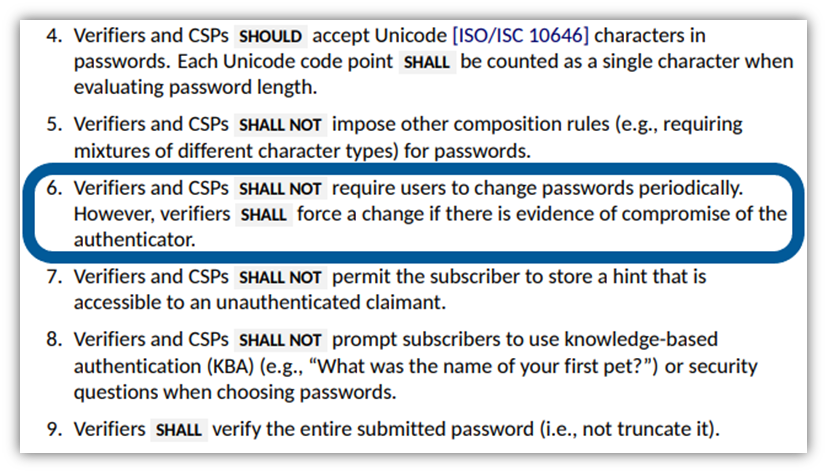
\ So, should passwords be changed proactively? Not necessarily, based on the National Institute of Standards and Technology’s (NIST’s) latest version of its Digital Identity Guidelines:
\
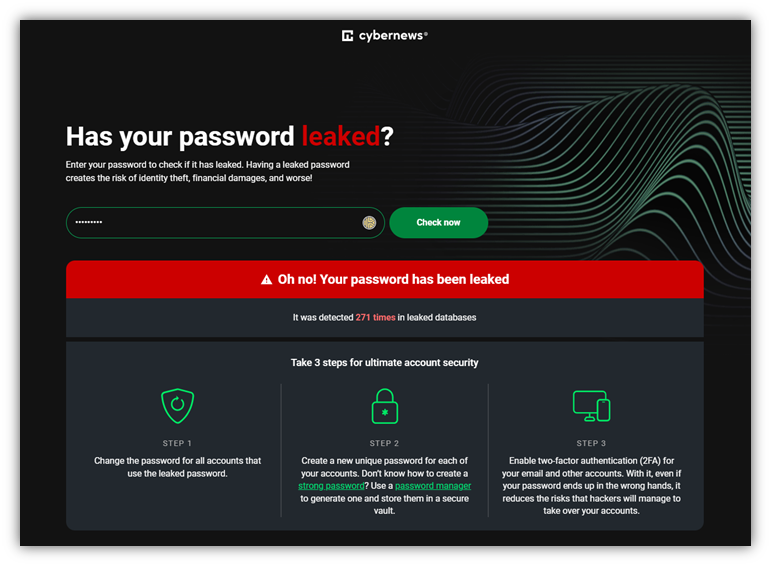
\ Not sure whether your password has been leaked or breached? Check out CyberNews’ password leak checker tool. Here’s an example of the results for the password NoWayJose:
\
\
12. The Number of Data Breaches in H1 2024 Skyrocketed2024 has been a record-setting year in many ways — certainly not the least of which includes the number of reported data breaches that have occurred thus far. The Identity Theft Resource Center (ITRC) reports that the number of data breach victims increased by a whopping 1,170% year over year from Q2 2023 to Q2 2024. No, that wasn’t a typo — you did read that correctly.
\ The ITRC reports that H1 2024 data breaches and other compromises totaled 1,571 and affected more than 1.007 billion victims. However, it’s quick to point out that the estimated 1+ billion victims don’t count those involved with the massive Change Healthcare-related supply chain attack, which is likely to “impact ‘a substantial number’ of U.S. residents.”
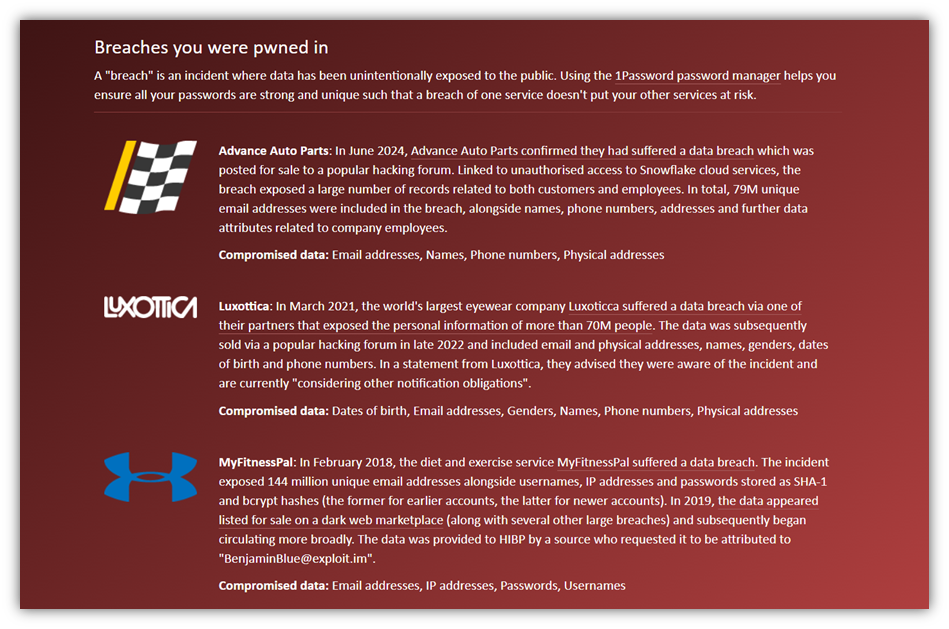
\ But how can you tell whether your information has been included in any breaches? One way to know is by checking online databases such as haveibeenpwned.com. Here’s a quick example of how it looks when you use this tool:
\
\
13. Unmanaged Devices Targeted in 90% of Ransomware EventsIt’s no secret that unmanaged network devices pose significant security risks to your organization. However, Microsoft’s 2024 Digital Defense Report indicates that in cases where ransomware attacks progressed to the ransom stage, they overwhelmingly use unmanaged devices as either the initial access vector or as the means to remotely encrypt assets:
\
“We observed remote encryption in 70% of successful cases, with 92% originating from unmanaged devices in the network, underscoring the need for organizations to enroll devices into management or exclude unmanaged devices from the network.”
\ This is why it’s crucial that businesses authenticate and manage their network devices. If that’s not possible, then the devices should be removed from the network to avoid potentially being exploited.
\
How the “Good Guys” Are Fighting BackCybersecurity experts, lawmakers, and organizations around the world are fighting back against these nefarious cybercrime activities. They’re increasingly looking toward AI-powered solutions to improve their cybersecurity defenses. Darktrace reports that 95% of the company’s 1,800 surveyed security leaders and practitioners indicate that AI-powered security tools will improve their organizations’ speed and efficiency when it comes to combatting cyber threats.
\ Here are a couple of other ways that some industry leaders are taking the initiative to curb cybercriminal activities.
\
Google Embraces Digital Certificates to Fight Cloud Account TakeoversMutual TLS (mTLS or what’s also called two-way authentication) is the use of digital certificates to prove that someone is who they claim to be. This is particularly useful when authenticating individuals and devices that are accessing your network, apps, and other systems remotely.
\ According to Google, certificate-based access uses mutual TLS to “ensure that user credentials are bound to a device certificate before authorizing access to cloud resources.” Basically, it’s about using digital certificates as device identifiers and verifiers when someone tries to access Google’s cloud services. According to the blog post:
\
“Even if an attacker compromises a user's credentials, account access will remain blocked as they do not have the corresponding certificate. This renders the stolen credentials useless.”
\
U.S. Secret Service Is to Investigate Cybercrimes Relating to Digital AssetsA new U.S. Senate bill titled “Combatting Money Laundering in Cyber Crime Act of 2024” (S.4830) aims to give the U.S. Secret Service agency the power to investigate the following:
\
“various crimes related to digital asset transactions and to counter transnational cyber criminal activity, including unlicensed money transmitting businesses, structured transactions, and fraud against financial institutions, and for other purposes.”
\ The bill was introduced at the end of July. If it passes, the new legislation would expand the Secret Service’s investigative authorities under Title 18 of the U.S. Code. It also requires the Government Accountability Office (GAO) to report its study of Section 6102 of the Anti-Money Laundering Act of 2020 and its evaluation of how well law enforcement identifies and deters money laundering-related cybercrimes.
\
- Home
- About Us
- Write For Us / Submit Content
- Advertising And Affiliates
- Feeds And Syndication
- Contact Us
- Login
- Privacy
All Rights Reserved. Copyright , Central Coast Communications, Inc.